“Kings” and “gods” of access: how the Russian-speaking hacker Fxmsp earned 100 million rubles on sales on the darknet

Today Group-IB introduced analytical report “Fxmsp: the invisible god of the network”, revealing the identity of one of the most active sellers of access to corporate networks of companies that provided their services on the darknet for about 3 years. During this time, he compromised about 135 companies in 44 countries. According to minimal estimates, Fxmsp’s profit over the period of its activity could be $ 1.5 million (about 100 million rubles). Despite the fact that Fxmsp was mentioned in public sources, Group-IB for the first time described in detail the progress of the investigation and facts not disclosed earlier. Materials on the identity of Fxmsp transferred to international law enforcement agencies.
Access is open
In October 2017, at the most famous Russian-language underground forum exploit[.]in appeared an announcement about the sale of access to corporate networks of a number of companies – a rare underground service for that time. Its author for the first time offered access to all critical segments of the networks of organizations compromised by him and said that among its victims there is a bank – a lot unique by the standards of the time.

October 1, 2017 – the “birthday” of Fxmsp, as one of the most famous sellers of access to corporate networks in underground forums. But this name became known around the world in May 2019, thanks to news about access to secure networks of three leading antivirus companies. Fxmsp copied various fragments of antivirus product code, analytics modules, development documentation, etc. from internal vendor networks.
This lot, as reported in the media, was put up for $ 300,000. Fxmsp wrote that it was a targeted campaign. It took him a little over three years to become one of the main players in the Russian-speaking underground from an ordinary user of a hacker forum who did not know how to monetize his hacking skills – with his pool of regular customers and even a sales manager.
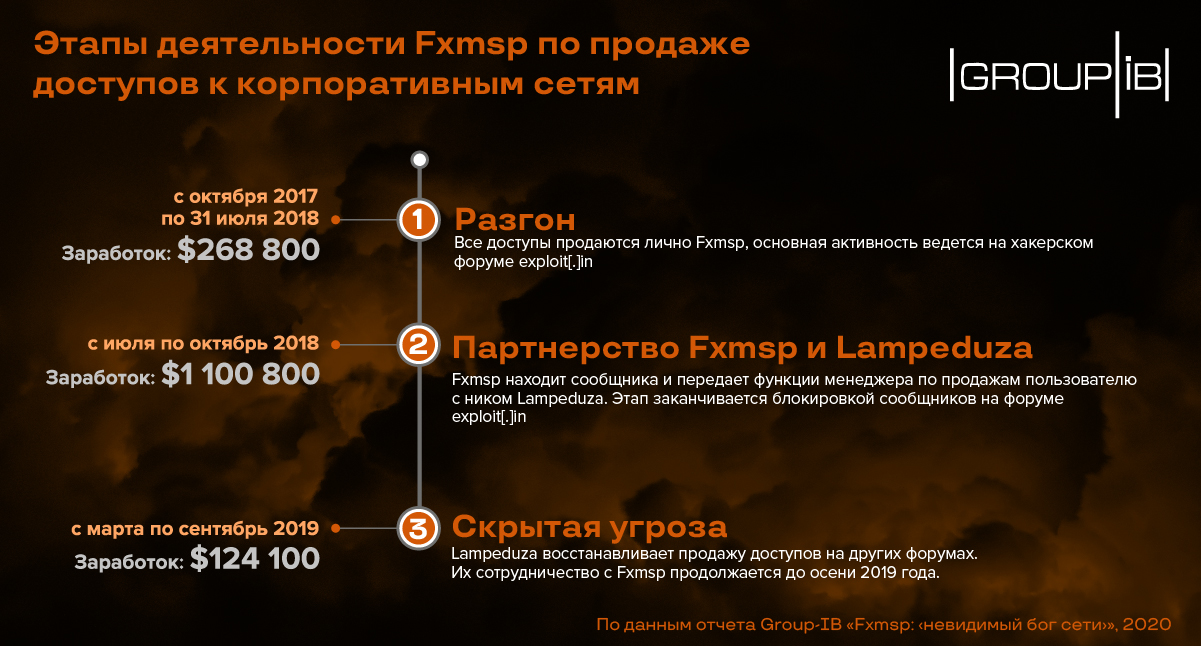
Examining activity at hacker forums for more than 17 years, Group-IB Threat Intelligence experts began to record the growth of offers related to the sale of access to corporate networks, starting in 2017 – with the appearance of Fxmsp on the hacker scene. At that time, the forums basically flooded offers on access to hacked sites, single servers, and accounts. In the second half of 2017, the seller with the nickname Fxmsp was the most prominent player and absolute leader in the number of lots in the “elite” niche of sales of access to corporate networks. Over time, he created a new trend in the underground community, making access sales not a product, but a service – providing privileged access to the network of victim companies for his customers.
The main activity of Fxmsp was in 2018. After that, the niche was empty for some time, and since the beginning of 2019, cybercriminals have had followers who today are active in the underground, using Fxmsp equipment. According to a Group-IB study, since the beginning of 2020, more than 40 cybercriminals have been trapping Fxmsp in the underground forums. In total, over 150 lots were sold during this time to sell access to corporate networks of companies in various industries.
By the time the scandalous news about the hacking of three antivirus vendors appeared, Fxmsp had actually completed its “public” activity. However, so far the most prolific “access seller” remains at large, posing a threat to companies in a wide range of industries, regardless of the country in which they are located. In this regard, the Threat Intelligence Group-IB team made a decision to prepare this report, transmit it to an expanded version of the international law enforcement agencies and make public the available materials on Fxmsp tools and tactics.
Market capture
The Group-IB report tracks Fxmsp from the first registration on the underground forum recorded by Group-IB Threat Intelligence to its disappearance from hacker sites. Fxmsp did not specialize in compromising specific companies. The top 3 victims are state organizations, IT service providers and retail. Among the companies attacked by Fxmsp was “big fish”: for example, 4 of them are included in the “Global 500 | Fortune ”for the year 2019. Fxmsp’s track record includes banks, fuel and energy companies, telecommunications operators, and energy sector organizations. One of them in the summer of 2020 suffered from an attack by a cryptographer. By this time, services from Fxmsp were not offered in the underground for 8 months.

The data obtained during the study using the Group-IB Threat Intelligence system allowed us to identify the tools that Fxmsp used to compromise companies, to determine, with a high degree of accuracy, the number of its victims, and to establish the alleged identity of the cybercriminal. The Group-IB report gradually reveals how, from the average user of the darknet, who started with cryptocurrency mining, in less than 3 years, the Russian-speaking hacker Fxmsp, according to the most conservative estimates, earned about $ 1.5 million – and this, excluding sales in “private” , lots without indicating the price, as well as repeated sales of accesses in the network of victim companies.
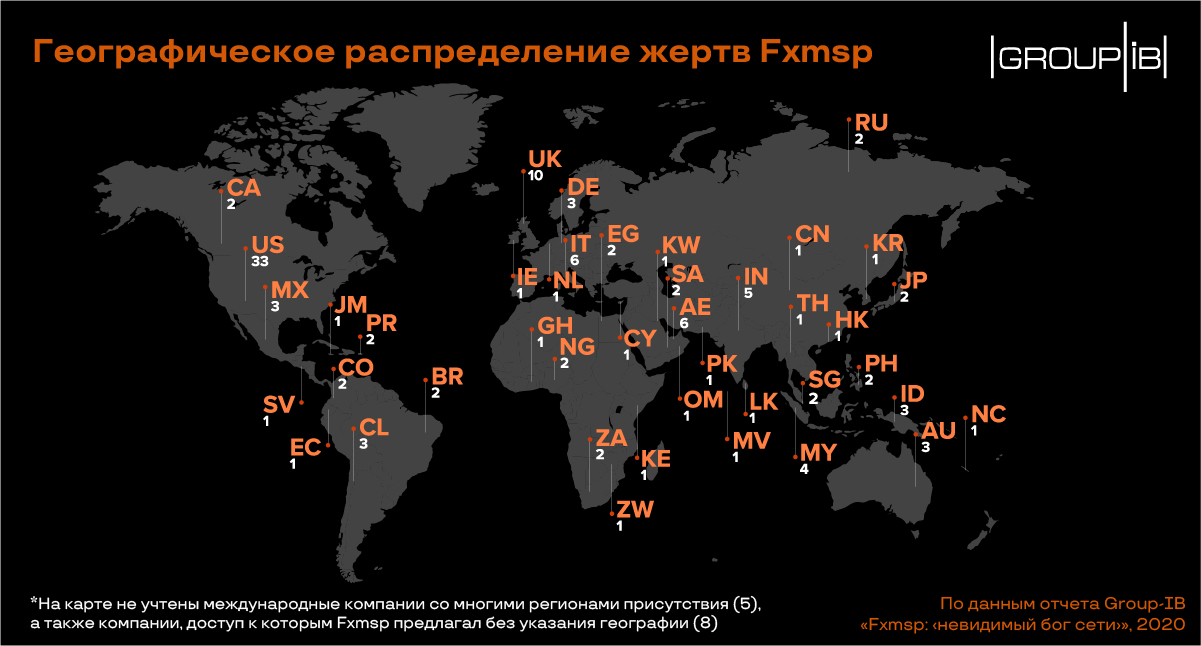
Together with their accomplice under the nickname Lampeduza, who took over the advertising and support of all transactions, from October 2017 to September 2019, they put up for sale accesses to 135 companies from 44 countries, including the USA, Russia, England, France, Italy, the Netherlands , Singapore, Japan, Australia and many others. Despite the unwritten law in the underground environment not to work “according to RU”, Fxmsp sold two lots for Russian victims, for which it was “banned” by the forum moderators, but this did not stop the criminal.
“The invisible god of the network”
The Group-IB report owes its name to one of Lampeduza’s advertising posts. Having gained credibility in the underground environment, the group acquired regular customers. Lampeduza was involved only at the monetization stage, while Fxmsp was involved in all stages of the attack, including scanning the IP range in search of the open RDP 3389 port, brute force, fixing to the network and installing backdoors.
“Selling access to corporate networks is still a rather rare service that is available on a limited number of underground resources, mainly Russian,” comments Dmitry Volkov, CTO Group-IB– More than 130 organizations all over the world have suffered from the activities of Fxmsp; he is one of the most dangerous criminals in his midst, possibly still continuing his activities. We want our study to speed up the detection and detention of the criminal hiding under the nickname Fxmsp and the people working with him, and to reduce the number of people who want to be his followers. That is why we decided to transmit an extended version of the report to international law enforcement agencies and made available materials on Fxmsp tools and tactics, showing how to protect against such attacks. ”
The nickname Fxmsp became widely known in May 2019 in connection with the appearance in the media of news about gaining access to the secure networks of three leading antivirus companies. One of them later partially admits the fact of access, assessing it as non-critical. By the time the scandalous news appeared, Fxmsp had actually completed its “public” activities. However, so far the most prolific “access seller” is likely to remain at large, posing a threat to companies in a wide range of industries, regardless of the country in which they are located.
You can download the report “Fxmsp: the invisible god of the network” here.