How Traffic Analysis Systems Detect MITER ATT & CK Hacker Tactics Using PT Network Attack Discovery

In the previous article, we examined the techniques of two tactics of MITER ATT & CK – initial access (initial access) and execution (execution), as well as using our NTA Solutions You can recognize suspicious activity in network traffic. Now we’ll show you how our technologies work with persistence, privilege escalation, and defense evasion techniques.
Persistence
Attackers use pinning tactics to ensure their continued presence in the attacked system. They need to be sure that even after restarting the system or changing credentials, their access to the system will remain. So they will be able at any time to control the compromised system, move along the infrastructure and achieve their goals.
Using traffic analysis, you can discover five pinning techniques.
1. T1133: external remote services
The technique of using external remote services to consolidate externally on the internal resources of the company. Examples of such services are VPN and Citrix.
What PT Network Attack Discovery (PT NAD) does: sees network sessions established via VPN or Citrix in the company’s internal network. The analyst can study such sessions in detail and make a conclusion about their legitimacy.
2. T1053: scheduled task
Using the Windows Task Scheduler and other utilities to program the launch of programs or scripts at a specific time. Attackers create such tasks, as a rule, remotely, which means that such sessions with the launch of task schedulers are visible in traffic.
What does PT NAD do?: if the domain controller sends XML files describing tasks created through group policies, our NTA solution automatically extracts such files. They contain information about the frequency of the task launch, which may indicate the use of the task scheduler for consolidation in the network.
3. T1078: valid accounts
Use of credentials: standard, local or domain for authorization on external and internal services.
What does PT NAD do?: in automatic mode, extracts credentials from the protocols HTTP, FTP, SMTP, POP3, IMAP, SMB, DCE / RPC, SOCKS5, LDAP, Kerberos. In general, this is a username, password, and a sign of authentication success. If they were used, they are displayed in the corresponding session card.
4. T1100: web shell
A script that is hosted on a web server and allows an attacker to gain control of that server. Since such scripts work in automatic mode and continue to function even after a server reboot, this technique can be used by cybercriminals even at the stage of fixing in the system.
What does PT NAD do?: Automatically detects loading of common web shells, accessing them via HTTP requests and sending commands.
5. T1084: Windows Management Instrumentation Event Subscription
Subscribing to events in WMI – technologies for managing components of local and remote operating systems. Attackers can use WMI to subscribe to certain events and trigger the execution of malicious code when this event occurs. Thus, attackers ensure a constant presence in the system. Examples of events that you can subscribe to: the onset of a certain time on the system clock or the expiration of a certain number of seconds from the moment the operating system starts.
What does PT NAD do?: Detects the use of the Windows Management Instrumentation Event Subscription technique using rules. One of them works when the network uses the ActiveScriptEventConsumer class of standard subscribers, which allows code to be executed when an event occurs and thereby attach the attacker to a network node.
For example, after analyzing the session card with the rule triggering, we see that this activity was caused by the hacker tool Impacket: in the same session, the detector for using this tool for remote code execution worked.

The session card in which the use of the Impacket tool was revealed. With its help, attackers use a standard subscriber to remotely execute commands
Privilege escalation
Privilege escalation techniques are aimed at obtaining higher-level permissions in the attacked system. To do this, attackers exploit the weaknesses of systems, exploit configuration errors and vulnerabilities.
1. T1078: valid accounts
This is identity theft: standard, local, or domain.
What does PT NAD do?: sees which user has logged in, whereby it is possible to identify illegitimate entries. One of the most common ways to increase privileges on a remote or local host that are running Windows is to create a Windows task scheduler task that will run on behalf of NT AUTHORITY SYSTEM, which makes it possible to execute commands with maximum privileges on the system.
Consider the case of creating such a task over the network using the ATExec tool. It is based on the components of the Impacket library and was created to demonstrate the library’s ability to work with the remote protocol for the task scheduler. Its work is visible in network traffic, and it well illustrates the technique of elevating privileges from the administrator level of a network node to the NT AUTHORITY SYSTEM level.
PT NAD automatically detected the creation of scheduler tasks on the remote host. The attack card below shows that the connection was made on behalf of the user contoso user02. A successful SMB connection to the ADMIN $ resource of the target host indicates that this user is a member of the local administrators group on the destination host. However, the XML description of the task indicates that it will be executed in the context of NT AUTHORITY SYSTEM (SID S-1-5-18):

Detecting Remote Task Creation Using ATExec Utility
Defense Evasion
This tactic brings together techniques by which an attacker can hide malicious activity and avoid detection by means of protection. Nine of these techniques can be detected using traffic analysis systems.
1. T1191: CMSTP (Microsoft Connection Manager Profile Installer)
Attackers are preparing a special malicious installation .inf file for the Windows Connectivity Manager Installer Profile Installer utility (CMSTP.exe). CMSTP.exe takes the file as a parameter and sets the service profile for a remote connection. As a result, CMSTP.exe can be used to download and execute dynamically connected libraries (* .dll) or scriptlets (* .sct) from remote servers. In this way, attackers can bypass the whitelist policy for running programs.
What does PT NAD do?: Automatically detects a special kind of INF file transfer in HTTP traffic. In addition to this, he sees HTTP protocol transmission of malicious scriptlets and dynamically-connected libraries from a remote server.
2. T1090: connection proxy
Attackers can use a proxy server as an intermediary to exchange data with a C2 server. So they avoid direct connections to their infrastructure and complicate the ability to detect them.
What does PT NAD do?: determines the use of the SOCKS5 protocol (it sends data from the client to the destination server through a proxy server invisibly to them) and an HTTP proxy. If connections via SOCKS 5 protocol or through an HTTP proxy server are associated with suspicious events, then such connections may indicate a compromise.
3. T1207: DCShadow
Creating a fake domain controller to bypass detection by SIEM systems, which allows malicious modifications to the AD scheme through the replication mechanism.
What does PT NAD do?: If DCShadow is used, a fake domain controller is created that does not send events to SIEM. Using such a domain controller, an attacker can modify Active Directory data – for example, information about any domain object, user credentials, and keys.
The use of such a technique can be identified by traffic. It clearly shows the addition of a new object to the configuration scheme of the domain controller type. The NTA system detects an attempt to attack DCShadow by detecting traffic specific to a domain controller from a network node that is not a domain controller.
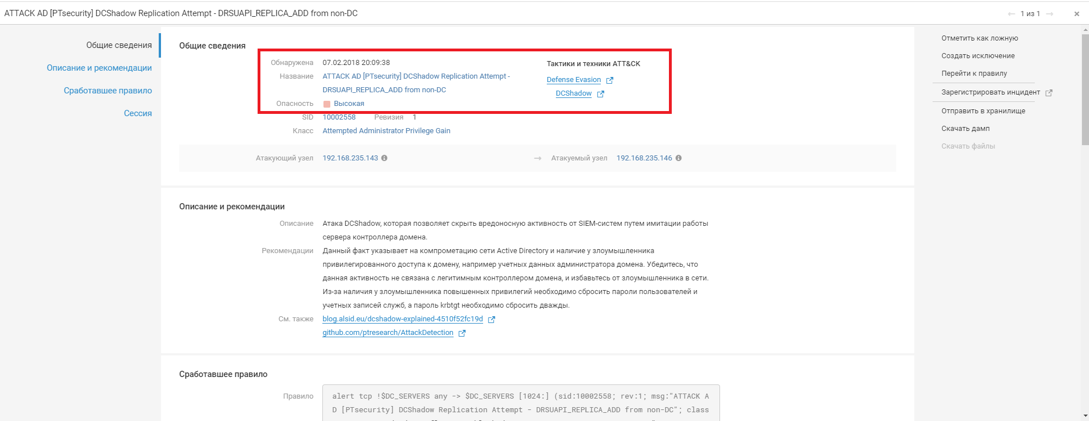
PT NAD recorded an attempt to attack DCShadow
4. T1211: exploitation for defense evasion
Exploiting vulnerabilities of the target system to bypass security features.
What does PT NAD do?: Automatically detects several popular exploitation techniques for vulnerabilities. For example, he identifies a technique for circumventing web application security based on duplication of HTTP headers.
5. T1170: mshta
Using the mshta.exe utility, which runs Microsoft HTML applications (HTA) with the .hta extension. Since mshta processes files bypassing browser security settings, attackers can use mshta.exe to execute malicious HTA, JavaScript, or VBScript files. Attackers use the mshta technique most often to bypass whitelisting policies for running programs and triggering SIEM detection rules.
What does PT NAD do?: Detects the transfer of malicious HTA files automatically. It captures files and information about them can be viewed in the session card.
6. T1027: obfuscated files or information
An attempt to make an executable file or network traffic difficult for security tools to detect and analyze by encrypting, encoding or obfuscating (obfuscating) its contents.
What does PT NAD do?: detects the transfer of executable files encoded using Base64, ROT13 algorithms or encrypted using gamma. Obfuscated traffic that some malware creates is also automatically detected.
7. T1108: redundant access
A technique in which attackers use more than one remote access utility. If one of the tools is detected and blocked, attackers will still have access to the network.
What does PT NAD do?: parses popular protocols, so it sees the activity of each network node. Using filters, the analyst can find all sessions of remote access tools installed from one node.
eight. T1064: scripting
Execution of scripts to automate various attacking actions, including bypassing whitelisting policies for launching programs.
What does PT NAD do?: reveals the facts of the transfer of scripts over the network, that is, even before they are launched. It detects the content of scripts in raw traffic and detects the transfer of files over the network with extensions corresponding to popular scripting languages.
nine. T1045: software packing
A technique in which attackers use special utilities to compress or encrypt an executable file to avoid detection by signature protection systems. Such utilities are called packers.
What does PT NAD do?: Automatically detects signs that the transmitted executable file has been modified using the popular packer.
Instead of a conclusion
We remind you that the full mapping of PT NAD to the MITER ATT & CK matrix published on Habré.
In the following articles, we will talk about other hacker tactics and techniques and how the PT Network Attack Discovery NTA-system helps to identify them. Stay with us!
Authors:
- Anton Kutepov, Specialist, PT Expert Security Center, Positive Technologies
- Natalia Kazankova, product marketer Positive Technologies




