How to get to IPVPN Beeline via IPSec. Part 2

By themselves, IPSec services are good, the service works through a cable Internet provider, but I would like to somehow reserve the inclusion or provide a service where there is no cable Internet, but only LTE.
In the classic version of MultiSIM Reservation, when providing IPVPN services over two mobile networks, there are the following problems:
- For each client, you need to create your own private APN, configure BGP or static routing in it, immediately calculate the required number of hosts for the correct IP addressing plan.
- The network of each telecom operator on the device must also be configured separately, taking into account the fact that each operator has its own characteristics.
- It is more difficult (much) to harass such an architecture.
- IPVPN traffic labels at the entrance to the LTE network are zeroed, that is, if telephony or video traffic is marked on all objects in your network, then when you enable IPVPN from pure LTE, traffic labels will be set to zero.
On the other hand, we have IPSec, in which all routing and client settings are abstracted from transport, whether it is a wired Internet channel or LTE of different operators, and traffic labels can also be stored inside the tunnel, albeit without ensuring SLA, since the Internet and especially LTE / 3G is a rather unpredictable medium for data transmission.
Therefore, we had an idea – “Why not use IPsec over LTE as well?” Put standard SIM-cards with pre-created APNs into routers and build IPSEC through them to our VPN HUB and release the client to its VRF. And if there is a wired channel, then use a wired connection as the main transport, and in case of an accident on it, switch traffic to LTE.
Thus, the network diagram began to look like this:
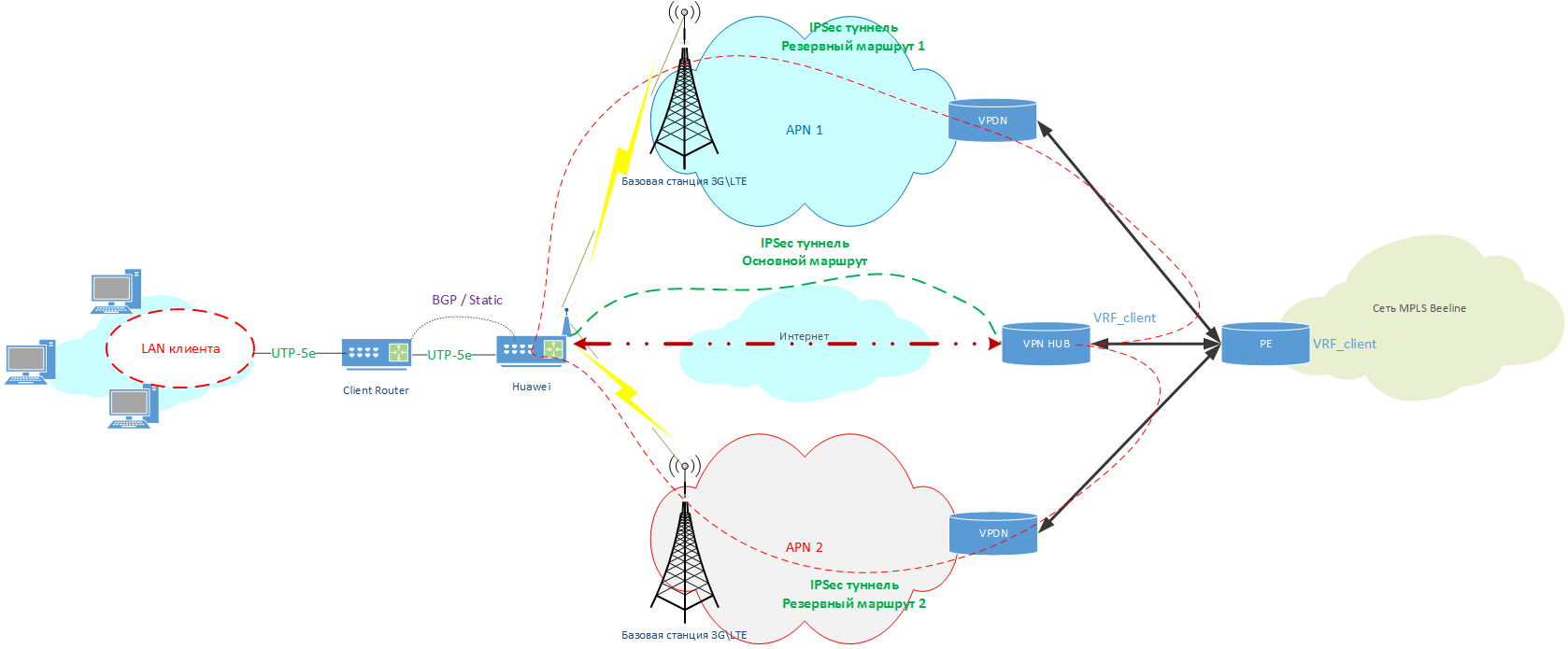
Clickable
The client gets up to three WAN channels at once, which will play the role of “underlay” for IPSec traffic:
- Wired Internet access channel.
- The first (main) LTE network.
- Second (Backup) LTE network (if needed).
Now it remains to select and configure a router for this service delivery option.
Configuring a router
When choosing a router, we were interested in two models from Huawei – AR161 and AR129. They have IPSec support, an LTE modem with support for two SIM cards, 4 Ethernet LAN ports + 1 Ethernet WAN, and the AR129 also has WiFi, that is, everything that is needed for our circuit to work, and even a little more.
But with the settings, everything turned out to be much more complicated.
While configuring routers for Multisim Redundancy, we faced the problem of priorities between wired WAN and two LTE networks to choose the best traffic route.
The Huawei AR161 / 129 has two tools for this:
- Network Quality Analysis functionality (aka NQA-test).
Conducts basic testing with icmp requests to the specified host to determine its availability. - Open Programmability System (OPS) + Python functionality.
A very powerful tool, it allows you to save information in logs and carry out “intelligent” switching based on icmp statistics, but also difficult to learn.
To solve our problem, we chose the OPS + Python functionality to enable only two LTE SIMs, and mixed mode for the Internet + two LTE SIMs.
An approximate configuration on routers is as follows:
In case of only 2x Sim LTE connection
# Configuring a dynamic IP address on a wired WAN interface (obtaining via DHCP)
interface GigabitEthernet0 / 0/4
ip address dhcp-alloc
# Configuring APN profiles, Cellular0 / 0/0 interface
apn profile [APN #1]
apn [APN 1 NAME]
apn profile [APN #2]
apn [APN 2 NAME]
sim-id 2
# Configuring Cellular0 / 0/0 interface
interface Cellular
dialer enable-circular
apn-profile [APN #1] priority 120
apn-profile [APN #2]
dialer timer autodial 60
profile create lte-default [APN #1] sim-id 1
profile create lte-default [APN #2] sim-id 2
ip address negotiate
modem reboot
# Setting the IPSec name
ipsec authentication sha2 compatible enable
ike local-name [IPSEC_LOGIN]
# Configure IPSec tunnel encryption parameters
ipsec proposal ipsec
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
ike proposal 1
encryption-algorithm aes-256
dh group2
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
# Configure IPSec tunnel authentication
ike peer ipsec_1
pre-shared-key simple [IPSEC_PASSWORD]
ike-proposal 1
local-id-type fqdn
remote-id-type ip
dpd type periodic
dpd idle-time 10
dpd retransmit-interval 2
remote-address 100.64.0.100
route accept
config-exchange request
config-exchange set accept
config-exchange set send
ipsec profile ipsecprof_1
ike-peer ipsec_1
proposal ipsec
# Configuring an IPSec tunnel
interface Tunnel0 / 0/0
tunnel-protocol ipsec
ip address [туннельный IP адрес на марш-ре Huawei] 255.255.255.252
source Cellular
ipsec profile ipsecprof_1
# Setting up routes
ip route-static 0.0.0.0 0.0.0.0 Tunnel0 / 0/0
ip route-static [VPN HUB INTERNAL ADDRESS] 255.255.0.0 Cellular0 / 0/0
In case of Internet + 2x Sim LTE-inclusion
# Configuring a dynamic IP address on a wired WAN interface (obtaining via DHCP)
interface GigabitEthernet0 / 0/4
ip address dhcp-alloc
# Configuring APN profiles, Cellular0 / 0/0 interface
apn profile [APN #1]
apn [APN 1 NAME]
apn profile [APN #2]
apn [APN 2 NAME]
sim-id 2
# Configuring Cellular0 / 0/0 interface
interface Cellular
dialer enable-circular
apn-profile [APN #1] priority 120
apn-profile [APN #2]
dialer timer autodial 60
profile create lte-default [APN #1] sim-id 1
profile create lte-default [APN #2] sim-id 2
ip address negotiate
modem reboot
# Setting the IPSec name
ipsec authentication sha2 compatible enable
ike local-name [IPSEC_LOGIN]
# Configure IPSec tunnel encryption parameters
ipsec proposal ipsec
esp authentication-algorithm sha2-256
esp encryption-algorithm aes-256
ike proposal 1
encryption-algorithm aes-256
dh group2
authentication-algorithm sha2-256
authentication-method pre-share
integrity-algorithm hmac-sha2-256
prf hmac-sha2-256
# Configure IPSec tunnel authentication
ike peer ipsec_1
pre-shared-key simple [IPSEC_PASSWORD]
ike-proposal 1
local-id-type fqdn
remote-id-type ip
dpd type periodic
dpd idle-time 10
dpd retransmit-interval 2
remote-address 81.211.80.50
route accept
config-exchange request
config-exchange set accept
config-exchange set send
ipsec profile ipsecprof_1
ike-peer ipsec_1
proposal ipsec
ike peer ipsec_2
pre-shared-key simple [IPSEC_PASSWORD]
ike-proposal 1
local-id-type fqdn
remote-id-type ip
dpd type periodic
dpd idle-time 10
dpd retransmit-interval 2
remote-address [VPN HUB INTERNAL ADDRESS]
route accept
config-exchange request
config-exchange set accept
config-exchange set send
ipsec profile ipsecprof_2
ike-peer ipsec_2
proposal ipsec
# Configuring an IPSec tunnel
interface LoopBack32
ip address [туннельный IP адрес на марш-ре Huawei] 255.255.255.252
interface Tunnel0 / 0/0
ip address unnumbered interface LoopBack32
tunnel-protocol ipsec
source GigabitEthernet0 / 0/1
ipsec profile ipsecprof_1
interface Tunnel0 / 0/1
ip address unnumbered interface LoopBack32
tunnel-protocol ipsec
source Cellular
ipsec profile ipsecprof_2
# Setting up static routing (towards the Beeline network)
nqa test-instance [username] inet
test-type icmp
destination-address ipv4 81.211.80.50
source-interface GigabitEthernet0 / 0/4
frequency 16
probe-count 2
start now
# Setting up routes
ip route-static 81.211.80.50 255.255.255.255 GigabitEthernet 0/0/4 dhcp track nqa [username] inet
ip route-static [VPN HUB INTERNAL ADDRESS] 255.255.255.255 NULL0 track nqa [username] inet
ip route-static [VPN HUB INTERNAL ADDRESS] 255.255.0.0 Cellular0 / 0/0 preference 70
ip route-static 80.240.216.155 255.255.255.255 GigabitEthernet 0/0/4 dhcp
ip route-static 194.67.0.206 255.255.255.255 GigabitEthernet 0/0/4 dhcp
Everything, the configured router can be installed to the client.
Plans
From plans to develop this solution:
- Do the same, but on Cisco / Mikrotik routers.
- Translate all switching logic to OPS + Python only
In the next articles we will tell you how we made the services friends Multisim Reservations with our Cloud PBX, made L2-over-L3 mode on the same huave using x-connect, put out scripts for switching SIM cards in Python and tell you about USB-Deployment on routers.
Thanks to my colleagues from RnD, especially Denis Zinchenko (Dzinch) and Andrey Voronov for preparing these technical solutions and for helping me write this article!
PS The first part of the post is here.