How to ensure network perimeter protection after foreign manufacturers leave the market

If we compare UTM / NGFW solutions of Russian and foreign production, then the latter, as a rule, will have a number of advantages:
· the performance of foreign equipment is higher than that of domestic analogues;
The probability of failures in the hardware of foreign devices is lower than in Russian ones due to the high build quality and the level of reliability of components;
functionality of imported equipment is richer than domestic (more protocols are supported, more functions are implemented inside protocols, etc.)
However, in a situation where the risks of disabling protection functions due to license revocation by the manufacturer or blocking connections from IP addresses of the Russian Federation have increased significantly, the issue of replacing foreign equipment with Russian is becoming more and more urgent.
In this article, we will look at how to change the information security infrastructure in order to maximize the strengths of foreign-made equipment, while avoiding potential risks in its operation.
Current state of network perimeter protection based on foreign-made UTM/NGFW solutions
Basic network perimeter protection based on UTM / NGFW solutions of foreign production is built using the following functions:
-
for integration into the network, dynamic routing protocols (BGP, OSPF) are used;
-
stateful firewalling is performed between public (Internet), corporate and DMZ segments;
-
application control (Application Control, DPI) is performed by category and individual applications;
-
intrusion detection (IPS) is performed;
-
web filtering (URL Filtering) of traffic by categories and individual resources is performed;
-
protection against targeted attacks is performed (Antivirus, Anti-Botnet, Sandbox);
-
SSL/TLS traffic is decrypted;
-
construction of VPN tunnels between the company’s offices (Site-to-site VPN), as well as the organization of remote access for employees (Remote Access VPN).
At the same time, modern UTM/NGFW solutions require constant access to foreign cloud services:
-
updates of software and equipment signatures are made from the manufacturer’s servers located abroad;
-
some services work in the manufacturer’s “cloud” (for example, cloud sandbox, URL filtering by category, etc.).
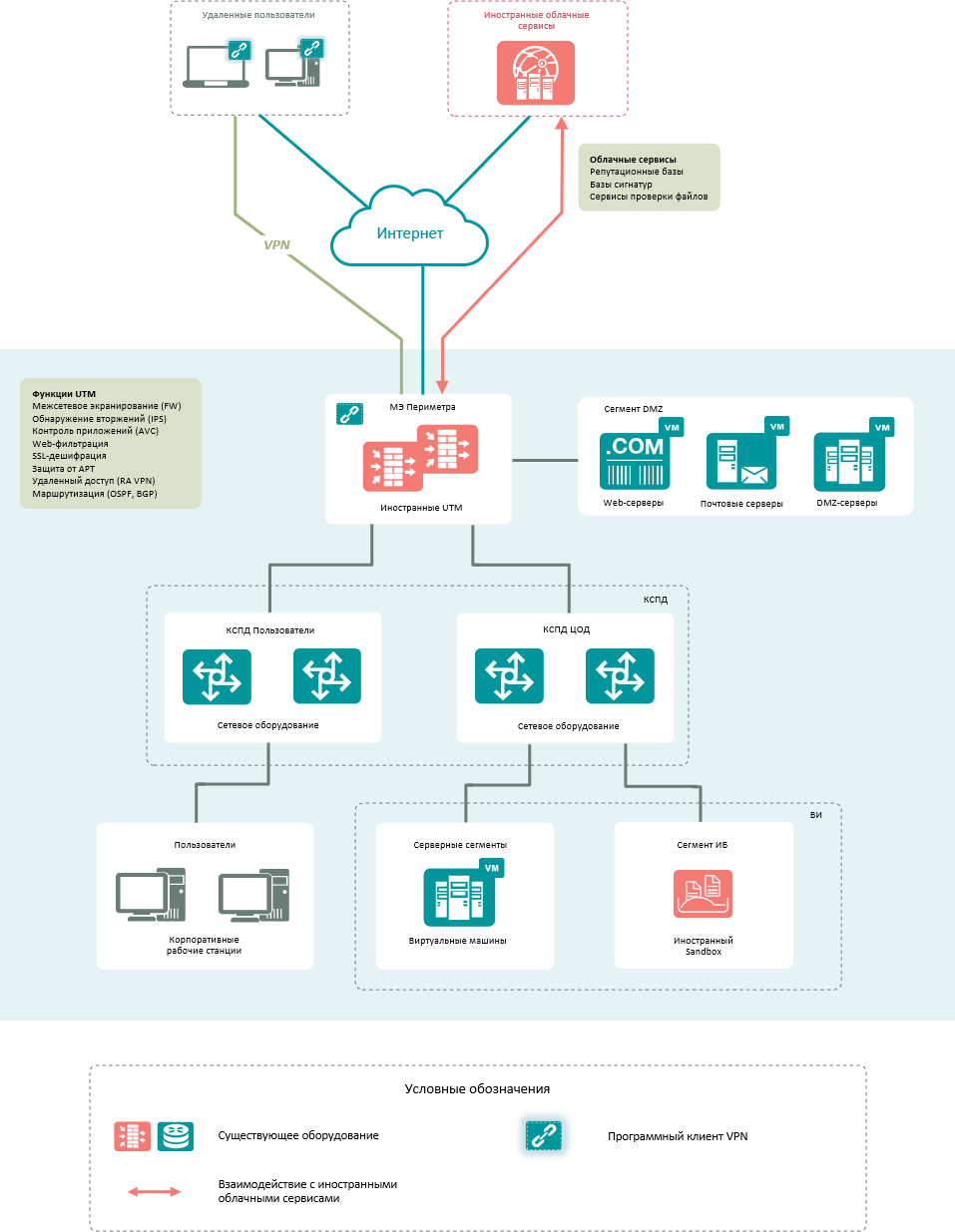
At the moment, companies are faced with many problems when using foreign-made protective equipment, among them:
-
lack of updating databases of protection tools (antivirus signatures, intrusion prevention, anti-spam, etc.);
-
disabling cloud components of protection tools (cloud sandbox, control of DNS and URL categories, cloud management and event collection servers, etc.);
-
disabling licensed features of the protection tool;
-
complete loss of control over the device;
-
unavailability of software updates to fix bugs and get new functionality;
-
unavailability of technical support from the manufacturer;
-
blocking access to the vendor portal to view the knowledge base and documentation;
-
the impossibility of acquiring renewal of subscriptions and technical support, expansion modules, equipment in spare parts;
-
inability to replace failed equipment;
-
the presence of “bookmarks” from the manufacturer, which he can share with foreign intelligence services.
Implementation of perimeter protection using Russian security tools
Based on the difficulties that have arisen, when replacing foreign equipment with Russian analogues, the optimal scheme will be in which:
-
foreign-made equipment retains all the functionality that does not require licensing and will work even in the worst scenario of a complete license revocation by the manufacturer. As a rule, this is a basic functionality that works reliably and does not require periodic updating of the hardware software;
-
functionality is transferred to domestic devices that does not work on foreign-made equipment without a license;
-
Russian equipment is installed between foreign devices and public networks to control traffic initiated by foreign products.
Thus, dynamic routing protocols (BGP, OSPF), stateful firewalling, and application control (Application Control, DPI) remain on foreign-made security tools.
In turn, the Russian-made equipment installed on the network perimeter is transferred to the functions of firewalling with connection state control (Stateful Firewall) between public (Internet), corporate and DMZ segments, application control (Application Control, DPI) by category and individual applications, detection intrusions (IPS), web filtering (URL Filtering) of traffic by categories and individual resources and decryption of SSL / TLS traffic. And the organization of remote access for employees (Remote Access VPN) is carried out through separate devices in the demilitarized zone of the network.
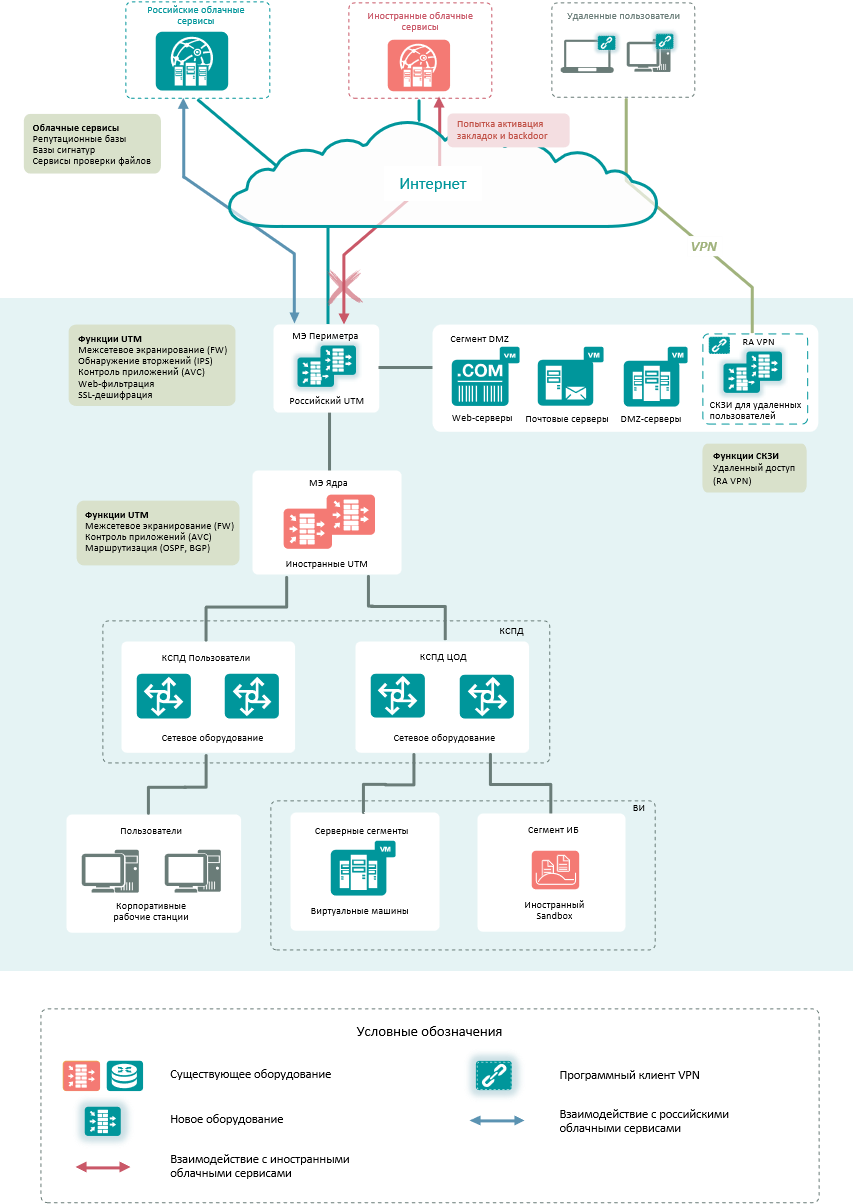
Implementation of protection against targeted attacks using Russian security tools
To protect against targeted attacks, foreign UTM/NGFW sent information for analysis to a “sandbox” hosted in the vendor’s cloud or on the organization’s site, or used specialized signatures – IPS, Anti-bot, C2, Antivirus.
Russian UTMs, as a rule, do not contain full-fledged built-in APT functionality, since different companies are engaged in the production of UTM solutions and means of protection against targeted attacks in our market.
More reliable protection against targeted attacks can be provided by domestic XDR class tools, the architecture of which is as follows
-
At the network level, XDR sensors (NTA, NDR) receive information about traffic at the network perimeter and in the KSPD/DPC segments using SPAN, ICAP, SSL Mirroring. This traffic is checked for signs of an intruder on the network using signature and behavioral engines. Files and URLs detected in traffic are sent to the sandbox (cloud or local) for verification, as well as to the manufacturer’s cloud to check the hashes of files and URLs against the Threat Intelligence database.
-
XDR agents (EDRs) are installed at the host level. Agents collect telemetry from hosts (security events, information about processes, work with files, registry, network traffic), detect suspicious activity in traffic, apply threat response actions if necessary (host isolation, collection of forensic information for subsequent analysis), send suspicious files and URLs for sandboxing.
-
The XDR (Sandbox) “sandbox” receives files and URLs for verification from network sensors and agents on hosts, checks them with signature, behavioral engines, and also launches them in an isolated environment with detailed inspection and logging of actions caused by the launched file.
-
The central node integrates all XDR components into a single system and provides a management interface for administrators and system operators.

Additional protections to create a second tier
To increase the overall level of infrastructure security, we recommend adding additional specialized protection tools to basic solutions (UTM, XDR).
-
Secure Web Gateway (SWG) – proxy servers with security features that provide protection for user web traffic, which requires a lot of computing resources, so its full implementation often lacks the capabilities of even the most powerful Russian UTM solutions. SWGs provide URL filtering by category, anti-virus protection, SSL decryption, control of transmitted content.
-
Secure Mail Gateway (SMG) – email security tools that provide protection against spam, phishing, viruses and other attacks.
-
Web application firewall (WAF) – provide protection for web servers when they are published on a public network. They implement the functionality of a reverse proxy server, advanced authentication options, SSL decryption, specialized protection against attacks on web applications.
-
Distributed Deception Platform (DDP) – solutions built on the basis of Honeypot technology implement a distributed infrastructure of decoys that are a bait for an attacker. When attempting to carry out an attack on a false target or using false information, the attacker reveals himself, which allows security personnel to quickly eliminate the threat.
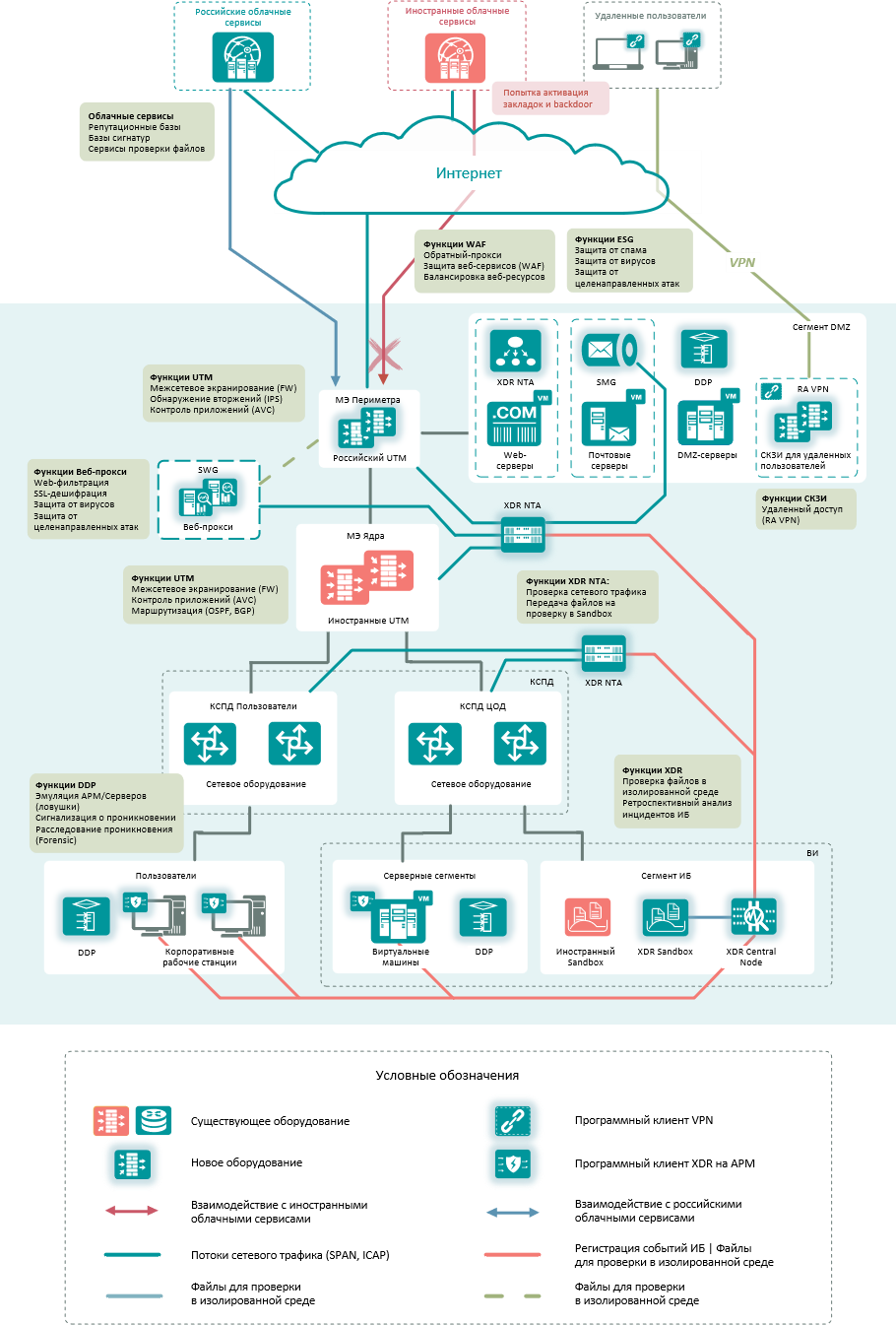
Examples of Russian means of protection for the creation of the second tier
conclusions
Using an integrated approach to create a second tier of protection using Russian means, it is possible to achieve a similar, and often superior, UTM / NGFW-solutions of foreign production, the level of infrastructure protection.
This approach also makes it possible to reduce the operating costs associated with previously purchased foreign equipment, since existing foreign UTM/NGFW solutions remain in the infrastructure to control traffic between internal network segments.
Authors:
Vyacheslav Monakhov, Head of System Engineering Department STEP LOGIC
Viktor Kolosov, system architect for complex information security projects STEP LOGIC