How Apple threw students from Russia or another criticism of the Apple Security Bounty program
Apple is renowned for caring for its users in terms of safety and usability. They generously reward security researchers who help fix vulnerabilities in their products. On the international stage, they have some of the highest awards. However, they are increasingly accused of unfair treatment of researchers who have found vulnerabilities on their platforms. An example of payments for vulnerabilities in Apple devices.

It is important to note that Apple is not represented on any of the bug-bounty sites, all bug reports must be sent directly to them. This allows them to control all information about the vulnerabilities found.
According to open information alone, over the past year the company has closed more than a dozen zero-day vulnerabilities in iOS.
Let’s take a closer look at their reward program.
Apple security bounty
As part of Apple’s commitment to security, we reward researchers who share critical issues with us and the methods used to exploit them. We prioritize resolving confirmed issues as quickly as possible to maximize customer protection. Apple offers public recognition to those who submit credible reports.
Requirements for receiving remuneration
Researchers should:
-
Be the first to report an issue to Apple Product Security;
-
Provide a clear report that includes a working exploit;
-
Do not publicly disclose the issue before Apple releases security advisories for the report.
The chain and report should include:
-
Both compiled and its source code;
-
Everything you need to complete the chain;
-
Sample of non-destructive payload if required.
Now let’s see how the Apple Security Bounty program works in practice using the example of the DoS vulnerability we found.
SkyWalk 0-day (
In order to cause a kernel panic, it is necessary to connect to the network distributed by a device running an operating system based on XNU (macOS, iOS, iPadOS), and send two packets to any Internet resource from port 0 to different destination ports. The result is a device freeze followed by a reboot. Below is a screenshot of the event logs (panic_full).
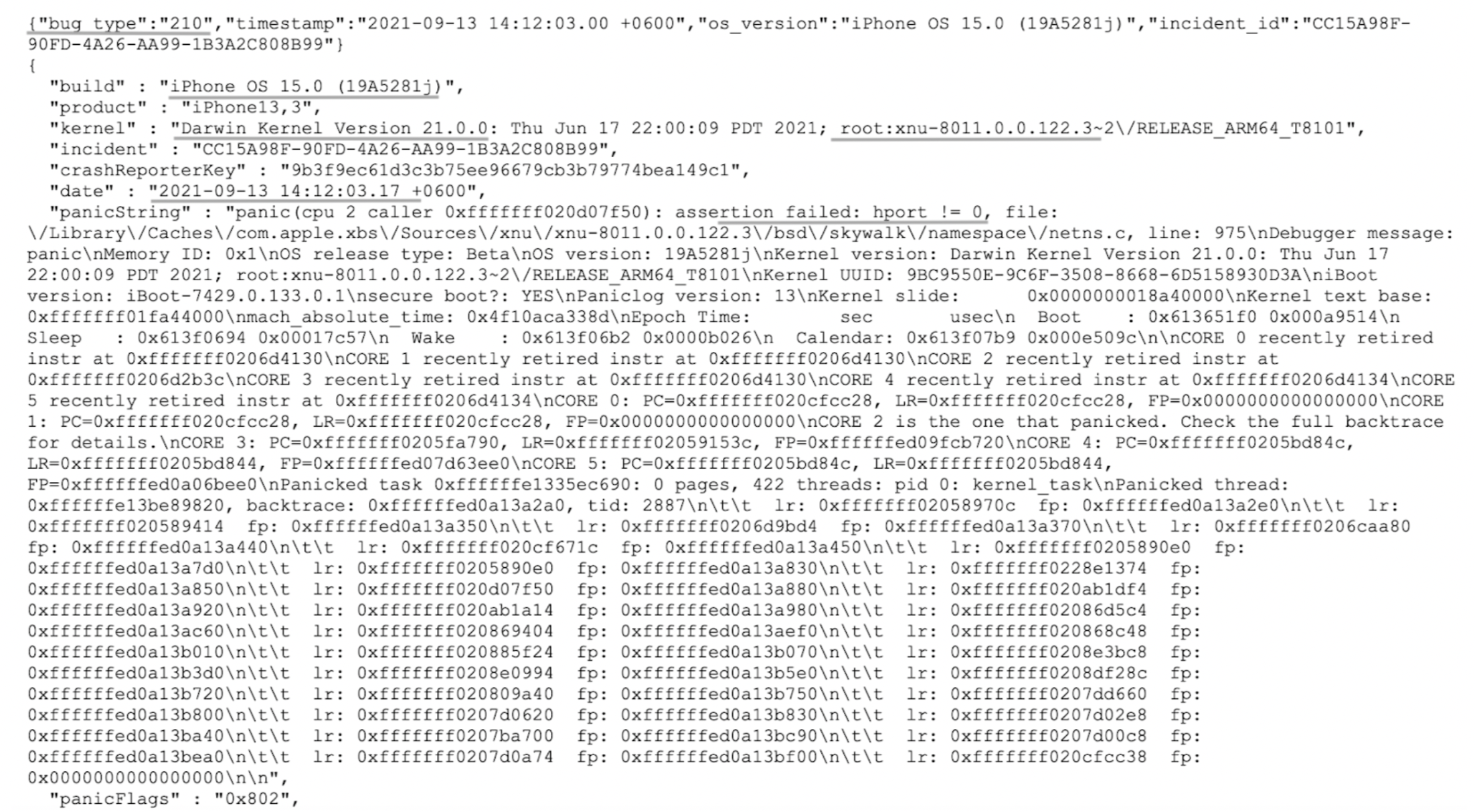
From the event log, we can distinguish:
Bug_type: 210.
Kernel version: XNU-8011.0.0.122.3 (also works with lower versions)
The logs lead us to the address “/Library/Caches/com.apple.xbs/Sources/xnu/xnu-7195.140.42/bsd/skywalk/namespace/netns.c” into the skywalk component. A web search led us to the book OS Internals by Jonathan Levin… Which describes the “mysterious” SkyWalk component. This book says that it is an “undocumented networking subsystem”.
The vulnerability affected XNU-based devices and was tested on:
-
iPhone 12 Pro (iOS 15.0);
-
iPhone 11 (iOS 14.7.1);
-
iPhone Xr (iOS 14.6);
-
MacBook Air, 2020 M1 (macOS 12.0);
-
Macbook Pro (Retina 13, Mid 2014) (macOS 11.5.2).
After collecting all this information, writing a PoC and a report, we hastened to notify the company. (PoC Source Code)
Reported security issue
Chronology of Events:
14 september we sent a report product-security@apple.com detailing the problem, how to reproduce it, and providing an executable PoC and its source code.

The next day, September 15th, we received a letter in which it was said about the initiation of an investigation, with a request to keep the information confidential.
1 october we have sent another letter in order to find out how the investigation is going and whether the attached materials are sufficient.
5 october a reply message has come. It said that the problem will be resolved in the next security update, and also clarified how we can be mentioned.

After that, a patch was released that disabled the ability to send packets from port 0, which made it impossible to attack from Apple devices. However, it was also possible to reproduce the attack from a linux system.
Some time later, a global update was released, in which the vulnerability was finally closed on all systems, while this vulnerability was not included in the list of fixes, just like mentions about us.
27th October we sent them a letter asking them to clarify the situation, but there was no response.

After a month and a half, we started writing an article, periodically sending letters to product-security.


On November 9, we were told that the vulnerability was confirmed for iPhone and iPad, and it was assigned a CVE identifier (CVE-2021-30924).
We were asked questions: why MacBooks were rejected and can we count on a reward.

On November 18, after 8 days, we were still mentioned in the macOS 12.0.1 security update, but there were no mentions in the updates for iOS and iPadOS, although the vulnerability was closed.
This concludes the communication from Apple.

Based on this situation, we can assume that Apple deliberately does not register on the bug-bounty sites to hide information about the vulnerabilities found and their number, as well as to complicate the receipt of rewards.
Epilogue
Since information about the vulnerability was reported more than 90 days ago, we consider it necessary to publish detailed information about it. Also, once again to warn researchers that Apple can throw not only with the payment of a fee for the vulnerability, but even with a free action in the form of an expression of gratitude for the work that Apple employees should have done.

Elaman Iskakov (@ darling_x0r) and Alexey Katkov (@ watman27).