Google-like IT Security Search vulnerability search – webinar announcement

IT Security Search is a Google-like search engine for IT that enables IT administrators and security teams to quickly respond to security incidents and analyze incoming events. The tool’s web interface consolidates disparate IT data from Quest’s many security and compliance solutions into a single console. Quest solutions, in turn, can be a reliable supplier of filtered data to various SIEM systems and even help to reduce the cost of ownership.
We invite you to register for the webinar, which will take place on June 16 at 11 o’clock Moscow time. You will learn about the functionality of the solution, tasks to be solved, integrations and licensing. Under the cut, briefly about the capabilities of IT Security Search. Even if you leave the data after the webinar, we will send you a link.
The tool integrates with other Quest solutions: Change auditor, InTrust, Recovery Manager and Enterprise Reporter. The data received from there is used for full-text search.
In IT Security Search, you can enter the username, workstation, event type, or whatever, and detect related events or configurations. Boolean expressions can be used to form queries. It is convenient to build reports from the query results and send them to interested parties on a schedule.
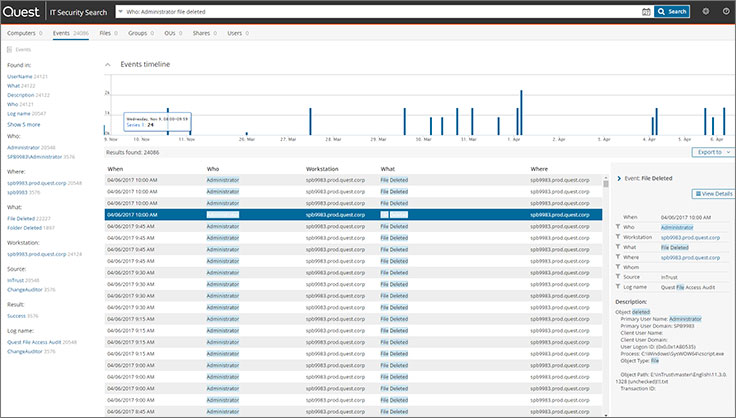
You can also rollback AD changes from the IT Security Search interface. That is, for example, you can restore a user deleted by mistake with all its attributes. This is done through integration with another Quest product – Recovery Manager for Active Directory.
If you would like to try Quest solutions on your infrastructure or get more information about products, leave a request at feedback form on our website or contact in another convenient way…
Links to our previous articles
Active Directory Group Policies (GPO): Understanding Why It Is Important And How To Manage Them In GPOAdmin
How to keep yourself and that guy safe as a Microsoft Teams admin
What useful things can be extracted from the logs of a Windows workstation
Access control and security reporting for the Microsoft environment in Quest Enterprise Reporter
Let’s compare tools for auditing changes in Active Directory: Quest Change Auditor and Netwrix Auditor
Sysmon can now write clipboard contents
We enable the collection of events about the launch of suspicious processes in Windows and identify threats using Quest InTrust
How InTrust Can Help Reduce RDP Login Failures
How to reduce the cost of ownership of a SIEM system and why you need Central Log Management (CLM)
We identify a ransomware attack, gain access to a domain controller and try to resist these attacks
Subscribe




