Exploring Cobalt cybergrouping: what new tools and attacks do hackers use
Specialists PT Expert Security Center track the activity of the Cobalt group since 2016. Today, the group is attacking financial institutions around the world. The damage from these attacks a year ago exceeded 1 billion rubles. Over the past four years we published some attack reportsrelated to this group.
During the past year, the Cobalt group not only modified its main CobInt tools and COM-DLL dropper in conjunction with the more_eggs JavaScript backdoor, but also used new delivery methods and new techniques to bypass protection at the initial stage of the attack. Updating tactics and tools may be due to the fact that the group has long been targeted by researchers from all over the world, and it needs to be one step ahead to bypass the means of protection.
On average, in 2019, the group carried out three attacks per month. In our new article – analysis of new tactics and tools of cyber grouping. Full study available link.
Phishing site European Central Bank
At the end of August 2019, while investigating information security threats, we recorded an attack using CobInt. The attack was allegedly aimed at European financial institutions. We have no data on how successful it was. A custom NSIS-installer served as a dropper for CobInt. We found three versions of such a dropper: for Chrome, Firefox, and Opera. Inside each was the same version of CobInt and the corresponding installer for the browser. After starting, the dropper saved CobInt to the% TEMP% folder, and the installer also launched it. After analyzing malware, we found that the distribution of droppers occurred from the phb site ecb-european[.]eu.

Phishing Site Home
The site was a copy of the site of the European Central Bank – except that when it was visited, the user was shown a pop-up window asking him to update the browser.

Popup on fake ECB website
As a result, the aforementioned dropper was downloaded to the user’s computer. In the source code of the page there was a link to the script that displayed this window.
Most likely, users got to the site using a phishing email similar to the ones that the Cobalt group most often uses.
2. Malicious VHD
At the end of December 2019, we discovered the next CobInt Cobalt bootloader. Unusual was the container that contained this bootloader. It was a virtual hard disk (VHD), which was supposedly mailed out.
The VHD format has been used since the creation of Hyper-V virtualization technology. A VHD file can contain everything that can be found on a regular HDD: disk partitions, a file system with folders and files. Starting with Windows 7, the user can manually connect the VHD, for example through the MMC console. Starting with Windows 8, a user can connect VHD simply by double-clicking on it with the mouse, and it will appear in the system as a regular disk.
In September 2019, the CERT / CC blog came out article the dangers of VHD files and their use as a potential vector in attacks. Will Dorman showed that neither antiviruses, nor mark on the web will not signal to the user that the contents of the VHD file downloaded from the Internet can harm the computer. It is possible that the Cobalt group used the results of this study. Their VHD file was also not detected by antiviruses at the time it appeared on VirusTotal. Six months later, this file is detected by just one antivirus: this is a very low indicator.
Inside VHD are two CobInt files. Two invalid Google certificates are attached to the end of one of the files to reduce the likelihood of detection by security features.
After the VHD is mounted, the user must manually start one of the files. By function, the two files are identical. After starting one of CobInt, the main library is loaded. The main library is loaded by CobInt from the control server as an HTML file.
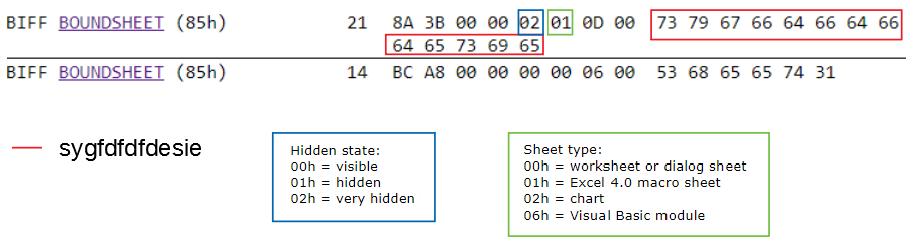
3. BIFF macro
In March 2020, we recorded a Cobalt group document in XLS format, which downloaded and ran a COM-DLL dropper. The document contained a fairly old Excel 4.0 macro format and was practically not detected by antiviruses (1 verdict out of 60 according to the VirusTotal service).
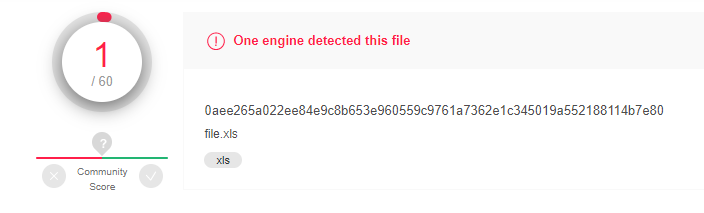
The number of antivirus verdicts the first time you download an Excel 4.0 macro file on VirusTotal
This macro standard has been around for 20 years. Its peculiarity is that the macro is not stored in a VBA project, it is located in the cells of the page, while the page can be hidden in Excel itself.
This means that the macro will not be in the VBA stream, but in the BIFF record (Binary Interchange File Format).
If you open the document in Excel, then we will see only one page and the absence of macros in the VBA project. However, Excel will still detect the presence of a macro and block its execution.
Opening the source document in the formula manager, we will see that one of the formulas starts automatically when you open the document.
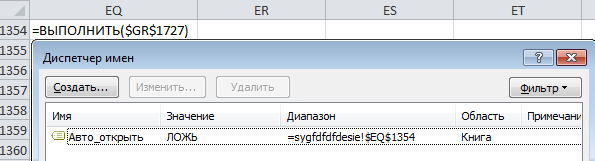
The macro formula that runs when a document is opened
The initial formula launches a large chain of COMBIN, EXECUTE, SYMBOL, CALL commands, which ultimately leads to loading and launching a COM-DLL dropper. The entire command chain is scattered across a huge field of cells in an Excel page, which makes analysis difficult.

Macro Formulas for Downloading and Running a COM-DLL Dropper
4. Analysis of COM-DLL dropper
In early April 2020, we discovered a new version of the COM-DLL dropper. In terms of functions, it differed from all that we saw earlier. However, the payload in the form of the more_eggs JavaScript backdoor remains the same.
The COM-DLL dropper appeared in the Cobalt arsenal in the summer of 2017 and is still used by the group to deliver a JavaScript backdoor more_eggs, which is contained in it in encrypted and archived form.
Features dropper:
- Fully written in PureBasic.
- Uses a large number of different anti-analysis techniques.
- It contains an encrypted and archived JavaScript loader, a JavaScript backdoor, a legitimate command line conversion utility for launching the more_eggs JavaScript backdoor.
- It has a built-in obfuscator for the JavaScript backdoor and the JavaScript loader wired inside.
Conclusion
The Cobalt Group continues to attack financial institutions around the world, takes on new tactics, updates tools, and tries to more effectively bypass defenses. Due to quarantine, many credit and financial sector employees are now working “from a distance”, out of reach corporate remedies. In addition, many attackers use the coronavirus theme in their attacks, such as Higaisa group. It is possible that the Cobalt group will try to use this theme in its future attacks.
Full study available here.
Authors: Denis Kuvshinov, Sergey Tarasov, Daniil Koloskov, PT Expert Security Center




