Experiments on people who have gone to “udalenka”

Along with the apocalyptic picture in information security, the picture of the effectiveness of remote work is no longer perceived as a synonym for procrastination, decline in productivity and uncontrolled work of employees. It is no coincidence that twenty percent of the employees of construction and industrial companies, who resumed their work in Moscow, continue to work at home, more than 500 employees of the VTB Contact Center remained remotely.
With this revolutionary transformation, the use of mobile devices has become one of its most important components, and today it is an axiom. Therefore, there is no more word on the relevance and effectiveness of corporate mobility, and all the attention hereinafter is on its safety.
Information Security Regulators Recommendations
Russian and European regulators in the field of information security promptly issued recommendations, including organizational and technical measures to protect corporate infrastructure during remote work.
In terms of organizational measures, it was recommended:
- To conduct an inventory of information assets, if hands had not reached before. Protecting “I don’t know what” is possible only “I don’t know how”.
- Limit the connection to the corporate network of personal devices, because it is generally impossible to protect them.
- Conduct educational conversations with the “personnel”, explaining the severity of the burden of responsibility for corporate secrets that fell on them. In order not to turn these conversations into idle chatter and corporate agitation for a just cause, formulate the rules in the simplest possible language, using illustrative examples. For instance:
- Do not connect to unknown WiFi networks, it is better to distribute the Internet from your phone.
- Do not download or open attachments from unknown sources, even if it is a coronavirus newsletter. Use official sources. So attackers will not steal access to your accounts and bank cards.
- Lock the screen when you move away from a computer or mobile device so that your children do not start working (… and spend what you earned instead of you … (Author).
- Do not send corporate meeting information to Zoom through unincorporated channels. Send it by mail so that outsiders do not connect to them.
Technical recommendations also do not look so harsh:
- Provide access to whitelists. Or, otherwise, prohibit users from everything except the minimum necessary and let only known devices into the network. Of course, this is a “stick”, but the “carrot” in this case will hit corporate security harder.
- Use certified protective equipment.
- Take into account the specifics of mobile devices:
- Limit the ability for users to install applications on their own. This is the main method of getting malware, which should be blocked, without waiting for the antivirus to trigger after the fact.
- Require the device to have a password and limit the number of attempts to enter it.
- Limit the maximum time the screen is inactive until it locks. As they say, trust, but verify.
- Install and timely update information security tools on mobile devices.
- Monitor mobile devices – monitor the installation of applications and locations of mobile devices, block the connection to the corporate network of hacked devices from root or jailbreak.
- In order to take into account the mobile specifics, in addition to the classic VPN solutions and antiviruses, you need to use UEM (Unified Endpoint Management) corporate mobility protection systems that have become corporate Active Directory in the world of mobility. We’ll talk about them in more detail below.
Practical advice from survivors
(may cause slight suffocation, sweating, but recovery is guaranteed): 
1. In no way can you rely on users.
Consider users to be babies who first see their hands. And this applies not only to field workers, for whom a corporate smartphone can be the first in their lives (especially in the regions), but also to managers. Give Android a smartphone to a leader who has been using only apple products for the past 10 years, and you will see that even OH is not a genius.
2. It is not enough to install only an antivirus and a cryptographic tool.
Still on the open spaces of the public procurement portal there are lots for the purchase of PROTECTED mobile devices complete with VPN and antivirus. Having at its disposal only this ascetic “gentlemanly” set, you can configure devices only once without further possibility to update protection tools or configure security policies on mobile devices.
3. Not all smartphones are equally useful, not all developers are equally experienced.
The cheaper the device, the more expensive it is to service and protect. All kinds of optimizers of cheap batteries do not allow not only the means of protection, but also business applications to work normally. Having bought such devices, one has to compensate for real security threats with fictitious organizational measures, believing that users never lose their mobile devices, themselves monitor the relevance and launch of the software and regularly update their own protection tools and only inside the controlled perimeter.
The belief of children in the existence of Santa Claus seems more justified.
Often, corporate business applications are written for corporate mobile devices. Over the years, we have seen a lot: both reports, the preparation of which eats the iPad in three hours, and six releases of one application per day. A separate volume of “mobility memoirs” can be devoted to managing application settings. Sooner or later, everyone comes to the conclusion that part of the application settings, for example, the server address or license, must be distributed remotely so that the user does not enter them manually. IOS and Android have built-in mechanisms for remote distribution of settings, but they are usually “remembered” after they have made their “unique” mechanism. The most “creative” way is to create separate builds of applications depending on the required settings. As a result, instead of delivering several lines with settings to thousands of devices, you have to deliver a 40 megabyte application.
Think about the manageability of your applications in advance.
4. Big bosses and humanities can not read further
Typical Remote Access Architecture: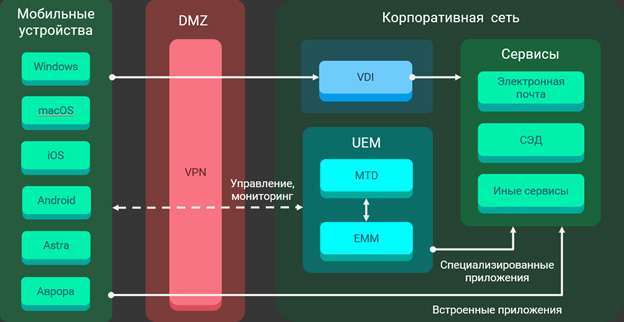
I. At the perimeter of the corporate network, the so-called In the demilitarized zone, in addition to firewalls and intrusion detection and prevention tools, VPN cryptographic gateways are installed that terminate all remote access traffic.
II. Remote access to corporate services can be organized using:
- Virtual Desktop Technologies, VDI. Using VDI, it is recommended to provide access to the most sensitive information that should not leave the corporate perimeter and be processed offline on mobile devices.
- Embedded applications preloaded on mobile devices. With a similar level of security, the functionality, stability and usability of applications, which are already used by hundreds of thousands of people, benefit.
- Specialized enterprise applications distributed to devices using UEM systems. Such applications are developed for those systems for access to which there are no built-in applications on mobile devices or which are inconvenient to work with from a mobile browser.
III. The UEM system has two functional blocks: corporate mobility management EMM (Enterprise Mobility Management) and security analysis of mobile devices MTD (Mobile Threat Defense). The second block includes the functionality of the antivirus and the so-called compliance, or, otherwise, checking the compliance of mobile devices with security requirements. In particular, the removal of corporate data when detecting signs of a device hacking.
IV. Client devices can be any. Together with traditional mobile devices based on Android and iOS, modern UEM systems allow you to control laptops based on Windows and macOS. Russian reality adds to this Astra Linux laptops and tablets, as well as mobile devices based on the Aurora OS. All this “zoo” needs to be managed and it is extremely desirable to have a single platform for this, and not an eclectic “stew” from the decisions of different vendors.
For instance, Safephone.
V. Since the IT services of almost all companies are now overloaded, they need a UEM tool that does not need to be dealt with constantly. I agreed with the security service on restriction policies, set them up, determined typical applications and their settings by user groups, and only occasionally do you monitor how users automatically connect. This should be sought.
Some more boring recommendations instead of conclusions
If you use corporate iOS devices, before issuing them to users, put them in supervised mode. This is such a special mode in which basic prohibitions and settings are available that do not require user confirmation. So using Apple technology is safer and more convenient. It is important to transfer to supervised mode before issuing the devicebecause iOS device backups contain a supervised indication. This means that the user will not be able to restore data from the backup device until it is transferred to the desired mode. It is terrible to imagine the reaction of a leader who was given a corporate iPad a year ago and is now being asked to give it to IT people for flashing with data loss from the backup.
Consider the “corporate” purchased mobile devices. The popularity of mobile devices in the consumer market is often determined by the ratio of price / quality, and the concept of quality is laid down mainly in hardware – the number of cores, processor clock speed, screen resolution, etc. Devices used on the corporate market need to be chosen differently, since their real value consists not only of the price of the hardware, but also of the man-hours required for their connection, configuration and subsequent maintenance, as well as indirectly from information security risks that are associated with their use. Do not buy devices that are too cheap. The money saved on their purchase is not enough for the salary of the staff serving them. Choose reliable manufacturers capable of ensuring the fast and safe use of mobile devices in your company.
Often when designing typical bans, the security service is guided by the principle “I don’t know why this is, so it should be banned.” This is correct from the point of view of information security, but after the next turn of the screw, the user can “break the thread” and he will put the corporate phone on charge forever, and he will use his personal phone with services that do not interfere, but help him work. Do not bend with safety.
Do not be afraid of the transition to corporate mobility.
If in doubt or questions, contact the professionals. SRI SOKB.