EV SSL Certificates: Is There Life After Death?
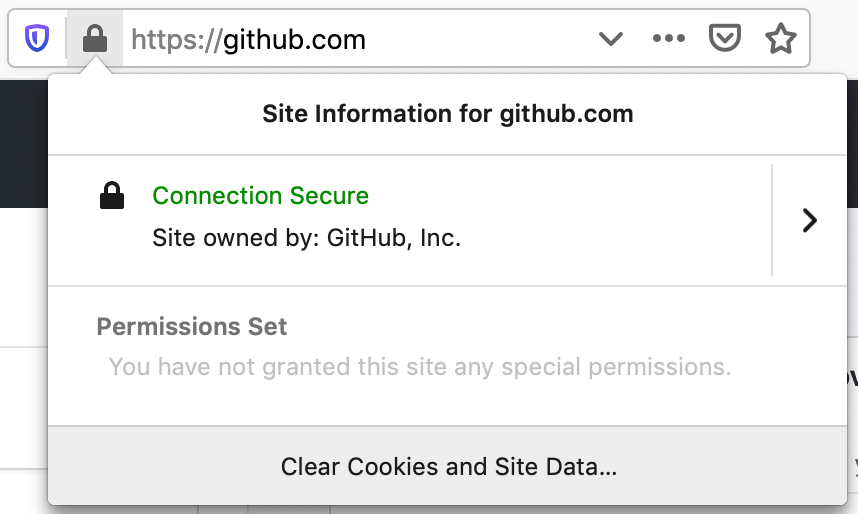
This is what the SSL SSL certificate information looks like in Firefox 70
Industry critics are pleased that the "air trade" will stop. But registrars themselves think EV SSL is too early to bury.
Extended Validation Certificates
Extended Validation Certificate (Extended Validation, EV) – A type of HTTPS certificate in which the certification authority performs an additional verification of the domain owner by linking the domain to the legal entity. The procedure itself can take up to two weeks. Similar to Know Your Client banking standards, the address and telephone number of the company are checked. This information is then embedded in the certificate and verified by a digital signature of the certification authority.
CN = www.bankofamerica.com SERIALNUMBER = 2927442 2.5.4.15 = Private Organization O = Bank of America Corporation 1.3.6.1.4.1.311.60.2.1.2 = Delaware 1.3.6.1.4.1.311.60.2.1.3 = US L = Chicago S = illinois C = US
Ordinary DV certificates simply confirm that the owner controls the domain specified in the certificate. At the same time, the certification authority does not have a clue who owns the domain and cannot contact it:
CN = whoami.com
These are actually anonymous certificates, useful only for encrypting traffic over HTTPS. They do not indicate the security of the site: anyone can get such a certificate through an automated procedure.
Previously, most browsers displayed the name of the legal entity and jurisdiction directly in the address bar, next to the URL, as shown in the illustration below.
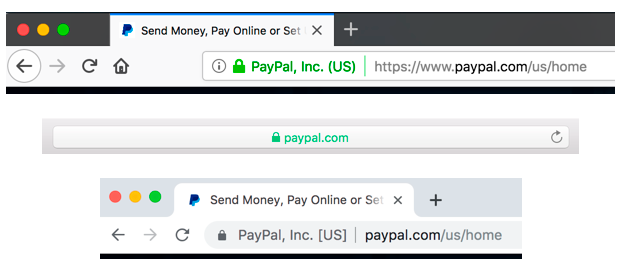
Previous UI for displaying EV certificates in Firefox, Safari, and Chrome browsers
Safari was the first to abandon this practice. He stopped displaying the name of the legal entity, and in the presence of an EV-certificate, the domain simply turns green. Then the Chrome interface changed.
Chrome 76
Chrome 77
On October 22, 2019, the final version of Firefox 70 is planned with the same change.

Firefox 69

Firefox 70
It should be noted that the guidelines of the CA / Browser Forum for EV (section 2) specifically indicate that the main purpose of EV certificates is to inform users about the legal identification of the business with which they interact through the website. The secondary goal is to combat phishing and other malicious types of web activity.
Why browsers have removed the EV SSL indicator
The main reason is the desire of developers to optimize the browser interface, since the long address bar does not fit on the screens of mobile devices. However, they could not sacrifice security for convenience. Google initiated a special study, based on which it concluded that the rejection of EV still not reduces security. This study lit a green light before changing the UI, which was required by interface developers for user convenience.
This is a study by Google’s interface design and security experts (Chrome Security UX group). They concluded that “EV UI does not provide user protection properly.”
Google notes that “the EV badge occupies valuable screen space, can display fake company names in the user interface, and prevents Chrome from moving toward a neutral rather than positive indication of secure connections.” According to the logic of Chrome Security UX specialists, the line with the EV certificate is a positive indication of TLS, while the neutral indication is more effective in terms of impact on users. Therefore, in the future, sites with HTTPS will be deprived of the "lock" icon, and for sites without HTTPS, a security warning will be displayed. This will encourage all sites to install SSL certificates.
A Google study noted the weaknesses of EV certificates:
- EV does not guarantee that the verified company does not violate the law, conducts an honest business, that it is truly safe and trustworthy.
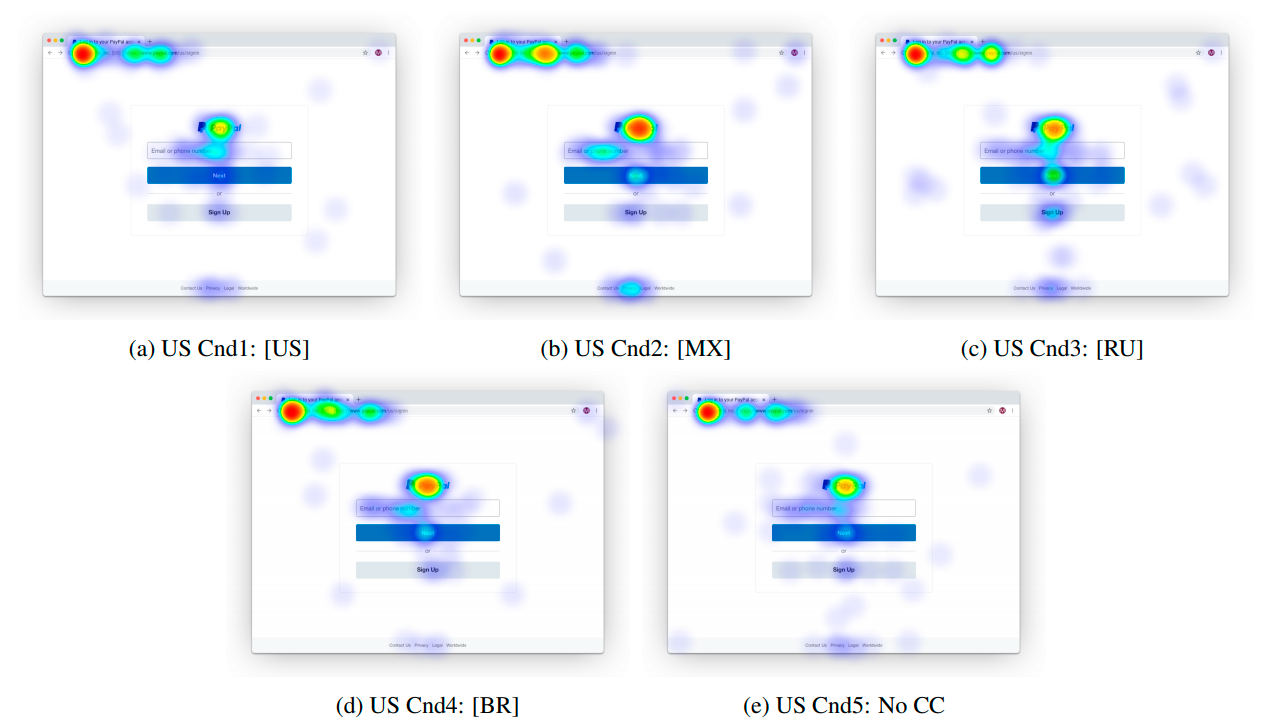
- EVs do not protect against phishing because users do not peer at them. In particular, they do not pay attention to the country code for the company for which the EV certificate is registered, which can be used for fraud.

Heatmap of the distribution of attention of Chrome users when demonstrating EV certificates with different jurisdictions, from a study of the Chrome Security UX group - Attackers can obtain an EV certificate for a company with a similar name.
- The legal name of the company is sometimes misleading, not coinciding with the name of the site. For example, a service for maintaining personal finances mint.com EV certificate issued by Intuit Inc.
What gives an extended check
The CA Security Council considers it a mistake to remove EV from the address bar. An organization that brings together a number of leading certification authorities provides the following arguments:
1. Only an EV certificate can confirm that a site belongs to a specific company. It is not possible to protect the confidential user data if we do not know which company owns the domain.
2. Protection against phishing. Studies show that cybercriminals actively use DV certificates, ordering them in thousands for free through an automated anonymous procedure.
As a result, phishing massively switched to DV certificates. The FBI has already issued a warning that users should not trust the HTTPS lock icon or the green indicator in the browser, since half of phishing sites show such an indicator.
At the same time, getting an EV certificate is difficult for fraudsters.
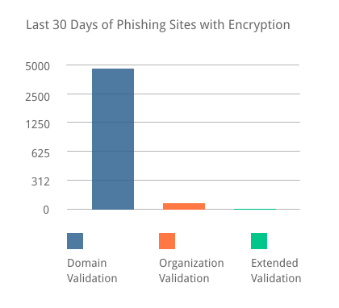
Here are the results of a study of 3494 phishing sites with SSL certificates in February 2019:
- EV: 0 phishing sites (0%)
- OV: 145 phishing sites (4.15%), mostly CDN multi-SAN multi-domain certificates like Cloudflare
- DV: 3349 phishing sites (95.85%)
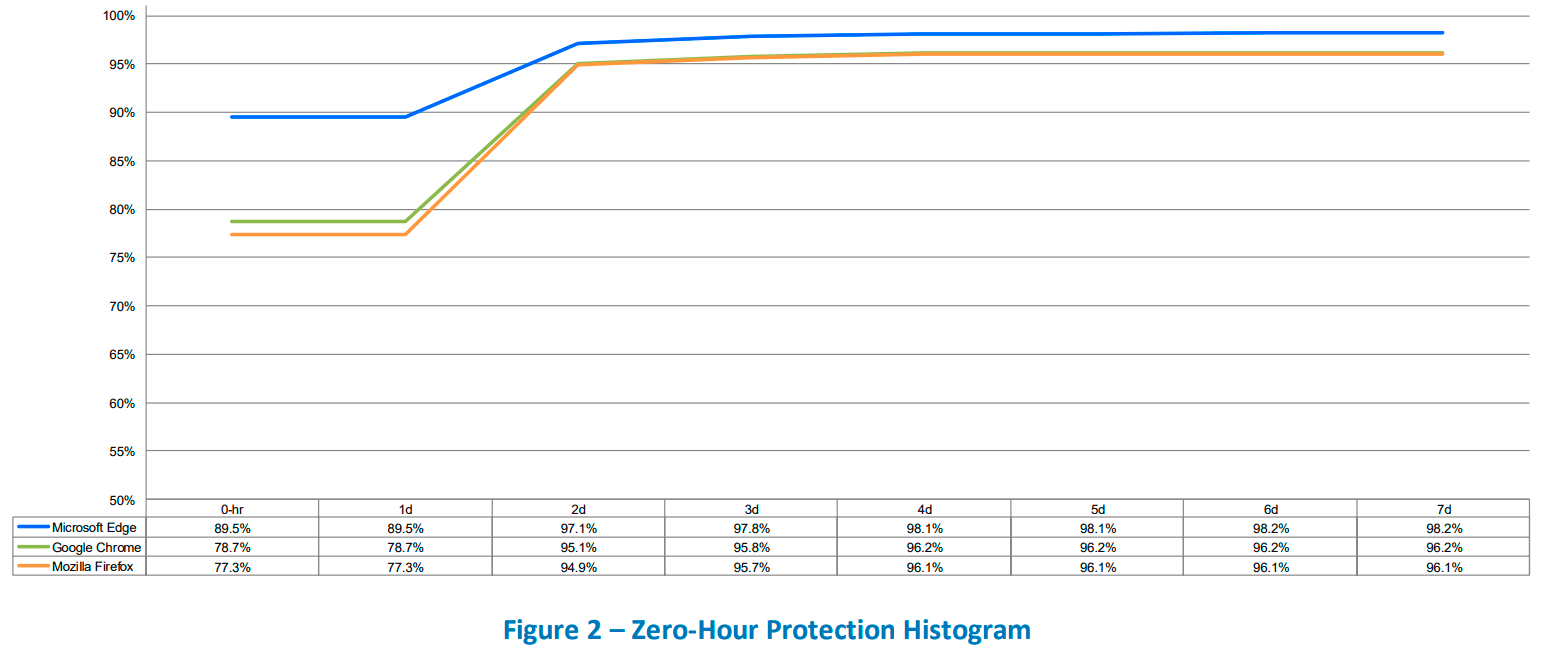
Browser antiphishing filters cannot cope with the threat. A NSS Labs study from October 2018 showed that Google Safe Browsing only recognizes 79% of phishing sites from the start. This percentage rises to 95% in two days, but by this time most of these sites stop working after completing their task.
3. CA Security Council considers Google’s thesis that the EV indicator can be rejected a mistake on the basis that users do not perceive it as a positive security indicator. Firstly, more qualified users still know the difference in certificate types. Secondly, it would be worthwhile to make efforts to inform less qualified users who do not understand the differences between DV and EV. Thirdly, the user's perception depends on the context: such simple measures as a seat belt in a car, people do not notice in normal comfortable conditions, but this is not a reason to abandon seat belts.
4. Relying on URLs alone is not enough for phishing recognition. Even a Google study notes that users have trouble analyzing URLs and often don’t notice errors and typos on phishing sites. At the same time, the EV indicator does not require URL analysis.
The CA Security Council believes that the shortcomings of current EV certificates are an excuse to work on improving them, not a reason for refusal. Statistics show that the EV certificate best eliminates phishing sites. To use it effectively, browsers should agree on standard indication, the Security Council believes, again citing an analogy from the automotive world: if the Stop sign is different from country to country and from state to state, and drivers do not understand its meaning, then this is no reason to remove Stop signs from all roads, because they are ineffective.
Despite the visual changes in browsers, EV remains a reliable security indicator. He still confirms the validity of the legal entity, just now this information has moved to another place. Users will have to click the lock icon to see this information.
So the rumors of the death of EV certificates were premature. It is likely that security experts and designers will understand the issue and adjust the interfaces. Now this issue is being discussed with browser developers.
GlobalSign Special Offer until September 30, 2019
Protect all subdomains with one certificate and save 30% of the cost!