DNS Security Guide
Whatever the company does, safety DNS must form an integral part of its security plan. Naming services, which translate hostnames to IP addresses, are used by virtually all applications and services on the network.
If an attacker gains control of the organization’s DNS, he can easily:
- transfer control over the resources that are in the public domain
- redirect incoming emails as well as web requests and authentication attempts
- create and validate SSL / TLS certificates
This guide looks at DNS security from two perspectives:
- Continuous monitoring and control of DNS
- How new DNS protocols such as DNSSEC, DOH and DoT can help protect the integrity and confidentiality of transmitted DNS queries
What is DNS Security?
There are two important parts to DNS security:
- Ensuring the overall integrity and availability of DNS services that translate hostnames to IP addresses
- Monitor DNS activity to identify potential security issues anywhere on your network
Why is DNS vulnerable to attacks?
DNS technology was created in the early days of the Internet, long before anyone even thought about network security. DNS works without authentication or encryption, blindly handling requests from any user.
In this regard, there are many ways to trick the user and fake information about where the translation of names to IP addresses is actually carried out.
DNS Security Issues and Components

DNS security consists of several basic components, each of which must be taken into account to ensure complete protection:
- Strengthening the security of servers and management procedures: improve server security and create a standard commissioning template
- Improving the protocol: implement DNSSEC, DoT or DoH
- Analytics and reporting: add a DNS event log to the SIEM system for additional context when investigating incidents
- Cyber Intelligence and Threat Detection: subscribe to an active threat intelligence channel
- Automation: create as many scripts as possible to automate processes
The above high-level components are just the tip of the DNS security iceberg. In the next section, we’ll take a closer look at more specific use cases and best practices that you need to be aware of.
DNS attacks
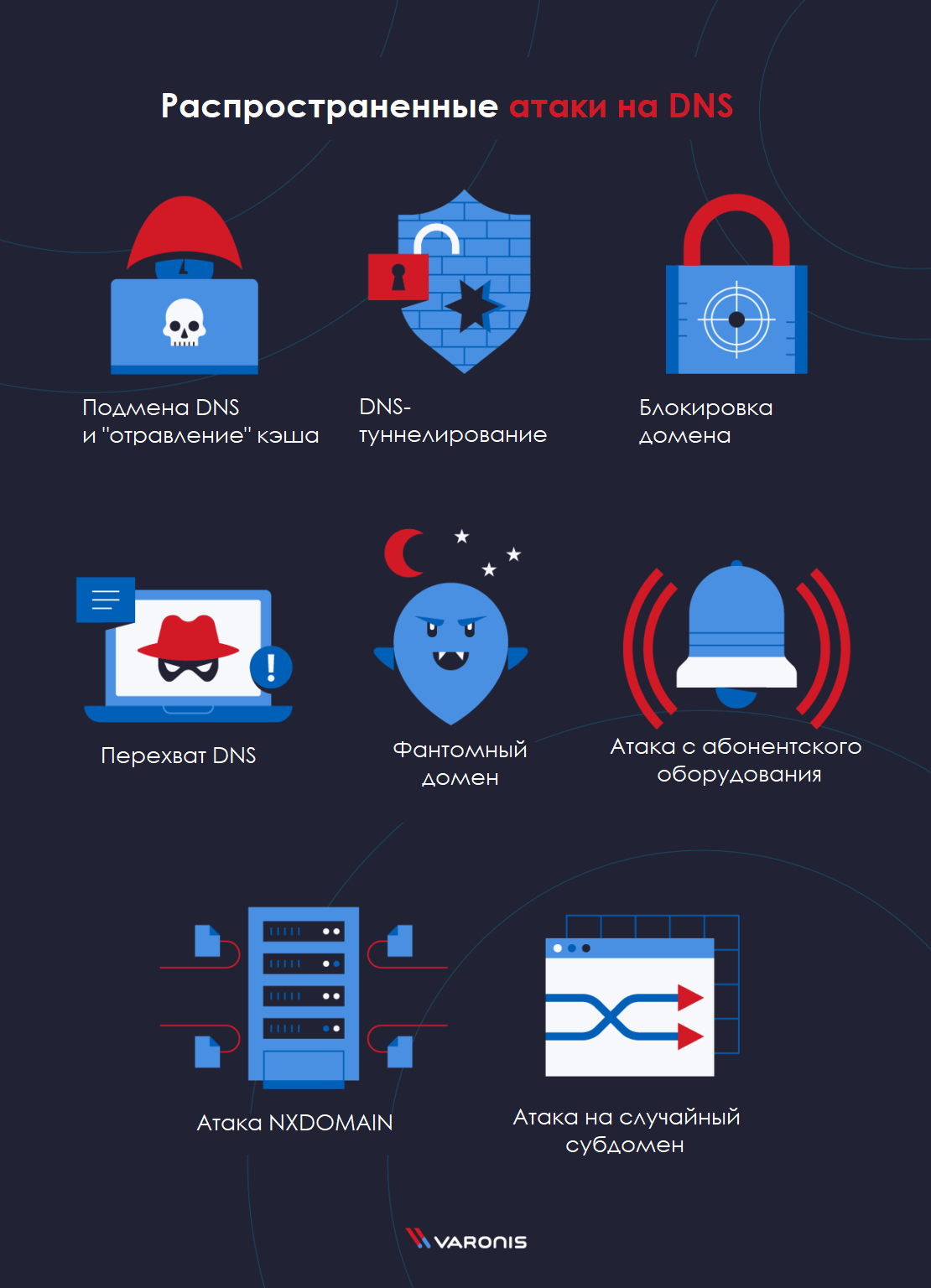
- DNS spoofing or cache poisoning: exploiting a system vulnerability to manage the DNS cache to redirect users to another location
- DNS Tunneling: mainly used to bypass protections against remote connections
- DNS interception: redirecting regular DNS traffic to another target DNS server by changing the domain registrar
- NXDOMAIN attack: Carrying out a DDoS attack on an authoritative DNS server by sending inappropriate domain requests to obtain a forced response
- phantom domain: forces the DNS resolver to wait for a response from non-existent domains, resulting in poor performance
- attack on a random subdomain: compromised hosts and botnets carry out a DDoS attack on a valid domain, but focus their fire on fake subdomains to force the DNS server to look up records and take control of the service
- domain lock: is sending multiple spam responses to block DNS server resources
- botnet attack from user equipment: a collection of computers, modems, routers and other devices that concentrate computing power on a specific website to overload it with traffic requests
DNS attacks
Attacks that in any way use DNS to attack other systems (i.e. changing DNS records is not the end goal):
- Fast-Flux
- Single Flux Networks
- Dual Flux Networks
- DNS Tunneling
DNS attacks
Attacks that return the IP address needed by the attacker from the DNS server:
- DNS spoofing or cache poisoning
- DNS hijacking
What is DNSSEC?
DNSSEC – Domain Name Service Security Modules – are used to validate DNS records without the need to know general information for each specific DNS request.
DNSSEC uses digital signature keys (PKIs) to confirm whether the results of a domain name query are from a valid source.
Implementing DNSSEC is not only best industry practice, but also effectively avoids most DNS attacks.
How DNSSEC works
DNSSEC works similarly to TLS / HTTPS, using public and private key pairs to digitally sign DNS records. General overview of the process:
- DNS records are signed with a pair of private and private keys
- DNSSEC responses contain the requested entry as well as the signature and public key
- Then public key used to compare the authenticity of the recording and signature
DNS and DNSSEC security

DNSSEC is a tool for checking the integrity of DNS queries. It does not affect DNS confidentiality. In other words, DNSSEC can give you confidence that the answer to your DNS query is not spoofed, but any attacker can see these results as they were sent to you.
DoT – DNS over TLS
Transport Layer Security (TLS) is a cryptographic protocol for securing transmitted information over a network connection. Once a secure TLS connection is established between the client and the server, the transmitted data is encrypted and cannot be seen by any intermediaries.
TLS is most commonly used as part of HTTPS (SSL) in your web browser as requests are sent to secure HTTP servers.
DNS-over-TLS (DNS over TLS, DoT) uses the TLS protocol to encrypt UDP traffic for regular DNS requests.
Encrypting these requests in plain text helps protect the users or applications making the requests from multiple attacks.
- MitM, or “man in the middle”: without encryption, an intermediate system between the client and the authoritative DNS server could potentially send false or dangerous information to the client in response to a request
- Spying and Tracking: Without encrypting requests, it is easy for intermediate systems to see which sites a particular user or application is accessing. Although it will not be possible to find out a specific visited page on a site from DNS alone, simple knowledge of the requested domains is enough to form a profile of a system or an individual
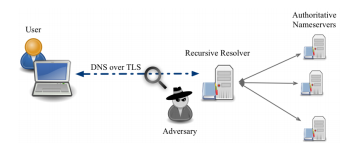
Source: University of California Irvine
DoH – DNS over HTTPS
DNS-over-HTTPS (DNS over HTTPS, DoH) is an experimental protocol jointly promoted by Mozilla and Google. Its goals are similar to DoT, which is to enhance the privacy of people on the Internet by encrypting DNS requests and responses.
Standard DNS queries are sent over UDP. Requests and responses can be tracked using tools such as Wireshark… DoT encrypts these requests, but they still identify as fairly clear UDP traffic on the network.
DoH takes a different approach and sends encrypted hostname resolution requests over HTTPS connections that look like any other web request over the network.
This difference has very important implications for both system administrators and future name resolution.
- DNS filtering is a common method of filtering web traffic to protect users from phishing attacks, sites that spread malware, or other potentially harmful Internet activity on a corporate network. DoH bypasses these filters, potentially putting users and the network at higher risk.
- In the current model of name resolution, each device on the network receives DNS requests to some extent from the same location (from a specified DNS server). DoH, and in particular its Firefox implementation, indicates that this may change in the future. Each application on a computer can retrieve data from different DNS sources, making troubleshooting, security, and risk modeling much more difficult.
Source: www.varonis.com/blog/what-is-powershell
What is the difference between DNS over TLS and DNS over HTTPS?
Let’s start with DNS over TLS (DoT). The main focus here is that the original DNS protocol does not change, but is simply transmitted securely over a secure channel. DoH puts DNS in HTTP format before making requests.
DNS Monitoring Alerts
The ability to effectively monitor DNS traffic on your network for suspicious anomalies is critical for early detection of a breach. Using a tool like Varonis Edge will give you the ability to stay on top of all the important metrics and create profiles for every account on your network. You can customize the generation of alerts as a result of a combination of actions that occur over a specific period of time.
Monitoring DNS changes, account locations, first-time use and access to sensitive data, and off-hours activity are just a few metrics that can be compared to provide a broader picture of discovery.