Choosing active protection methods using MITER
Came into our field of vision Matrix Shield from MITER, which provides tactics of active protection against malicious actions. Unlike ATT & CK matricesthat many people know, respect and use, the Shield is not so well known. However, the tactics described in it will help you more effectively resist attacks.
Attackers are very resourceful and rarely give in to difficulties. Therefore, active defense methods that involve studying their behavior, tracking their actions and responding in real time will always be relevant.
The classification of protection methods familiar to all of us is as follows:
cryptographic protection methods that change the type and structure of information during transmission over the network and during storage;
organizational methods of data protection;
technical and technological methods of information protection, implying the use of special software and hardware.
All of the methods below can be called static:
configure an information security system to prevent an attacker from breaking into the infrastructure;
configure access rights for users;
set minimum privileges …
…etc. They are united by the fact that they practically do not involve any interaction with the attacker. But this is how you can not only learn much more about his intentions and tools, but, of course, prevent him from moving deeper into the protected infrastructure.
The purpose of active defense methods is to prevent the actions of attackers immediately at the moment of their implementation, or even anticipate them. In addition, active protection includes the collection of information about the capabilities of the attacker. MITER specialists offer following tactics active protection.
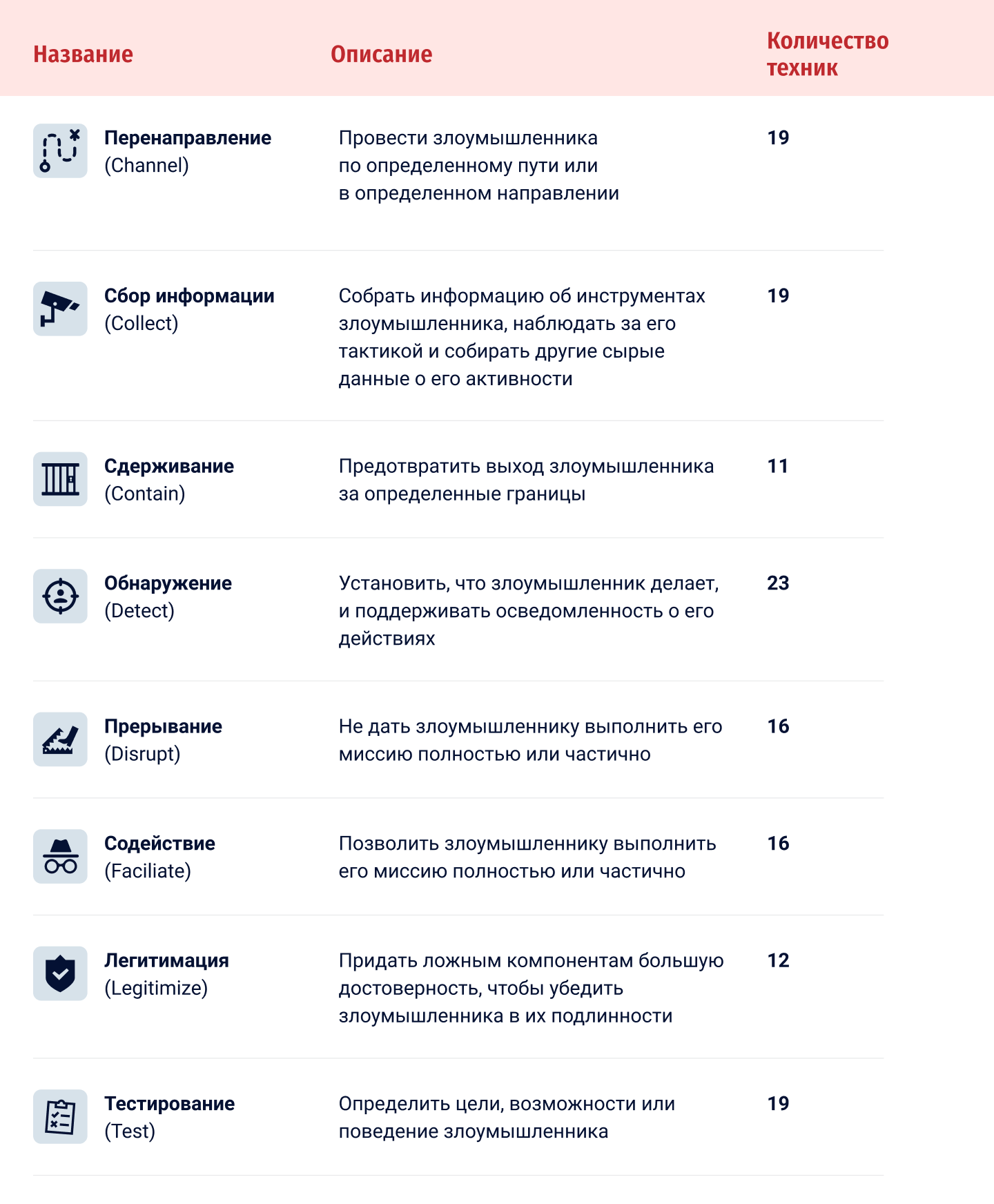
Now more about each of the tactics.
Redirecting
In our case, sending an attacker down the wrong path is a great idea. For example, it can be distracted from important systems and network segments by redirecting to fake ones, the loss of control over which will not harm the real infrastructure.
Thus, an attacker will waste time, resources and motivation, and information security specialists will be able to study his behavior.
Collection of information
All actions of an attacker can be recorded and studied to make the system infrastructure more secure. Gathering information about the attacker and his actions includes logging and collecting samples of the malware used.
Containment
An attacker can be framed. To do this, you need to provide a closed environment from which he can not get out and harm other parts of the infrastructure. This can be, for example, denying access to certain systems and subnets. Such measures are aimed at preventing lateral movement attacks.
Detection
The actions of the attacker must be detected before they can be somehow reacted. The system should be configured to notify that the attacker has reached certain points.
Interrupt
An attacker’s actions can be thwarted by making their tasks more difficult or by increasing control. So he will have to spend more resources and time.
Promoting
Yes, you heard right. The enemy can be helped to complete his business. You can use unprotected versions of OS or software, weak passwords; open ports, but only where it will not harm your infrastructure.
Legitimation
It never hurts to give authenticity to false components in order to convince an attacker of a realistic setting. These can be pseudo-real accounts, files, system operations – in short, everything that an attacker can get to.
Testing
As part of testing, an attacker can be provided with opportunities to infiltrate the system and check if he is interested in certain content. You can also complicate the tasks facing him in order to find out the level of his training.
Of course, it is impossible to apply all the tactics at once, so it is worth choosing the options that are suitable for the protected infrastructure. Each tactic has certain technicians, and the same technique can be used in different tactics. In the description of each protection technique, the methods used by the attackers are also listed, which will help you better navigate when choosing the tools to protect the system.
Note that the developers of Shield from MITER invite everyone to participate in the work on the matrices. They are open to new ideas.