Case Studies for Network Anomaly Analysis Tools: Remote Access Control
It should be noted right away that monitoring remote access is not much different from some other nodes. For example, in the last post, when we caught the DNSpionage and Sea Turtle campaigns, we started by grouping the DNS servers into a group, which we put in control, and which also served as our standard and the appearance of any nodes that perform the functions of a DNS server, but not included in the desired group would automatically be considered an anomaly. With remote access, everything is the same – first we must group all the internal IP addresses of remote users, as well as all the nodes to which these users can connect (for example, an RDP proxy, terminal server, email server, file server, work places to which users are remotely connected, or virtual machines accessed via VDI, etc.).
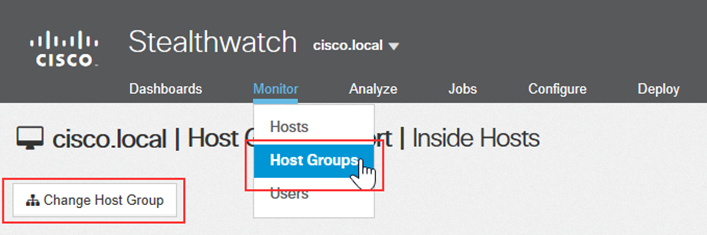
As an illustration, we will use the Cisco Stealthwatch Enterprise solution, in which we create the Remote VPN IP Pool group.

Further, we simply analyze all the activity recorded in relation to this group.
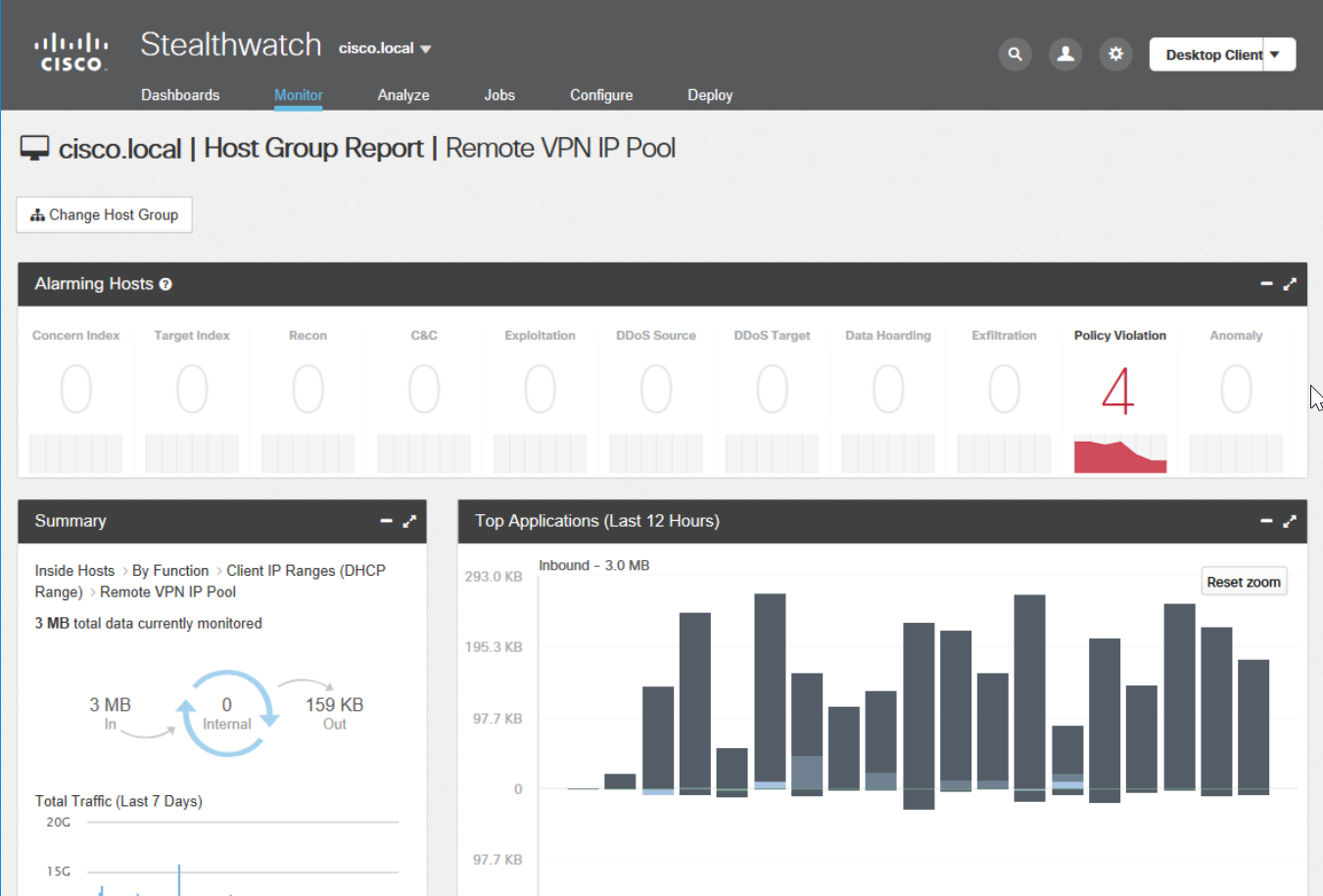
Please note that the system already shows us 4 violations of security policies. But now we look a little the other way. The “Top Applications” widget allows us to see all the incoming and outgoing traffic, grouped by application / protocol type.
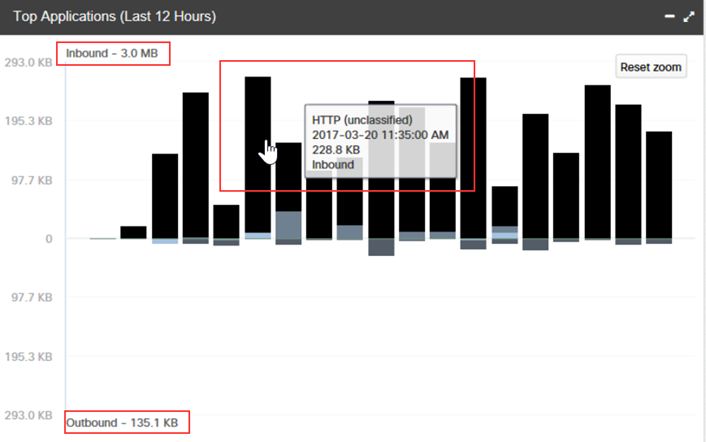
Further, we can go deeper to the desired depth in order to obtain details of who is communicating with whom, in what direction and in what volume.

For example, this is how the result of analyzing network traffic using the HTTP protocol associated with a group of remote nodes will look like.
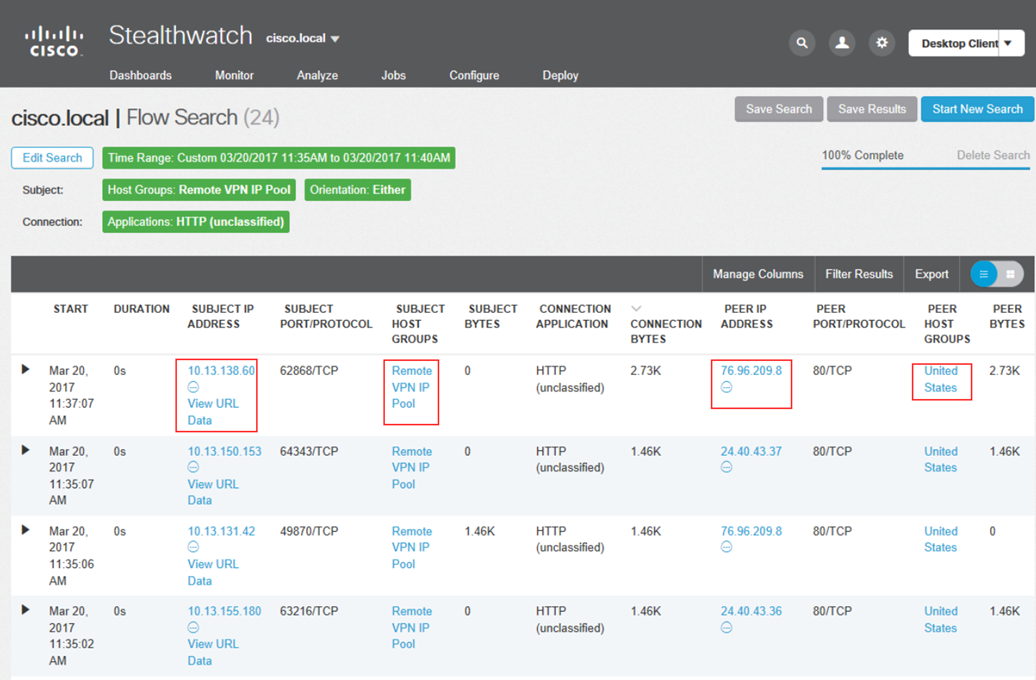
Further, we can use the Host Summary dashboard, which will show activity for each of the nodes of interest to us:
- who does the node interact with
- applicable monitoring policies
- host applications and activity of such use.
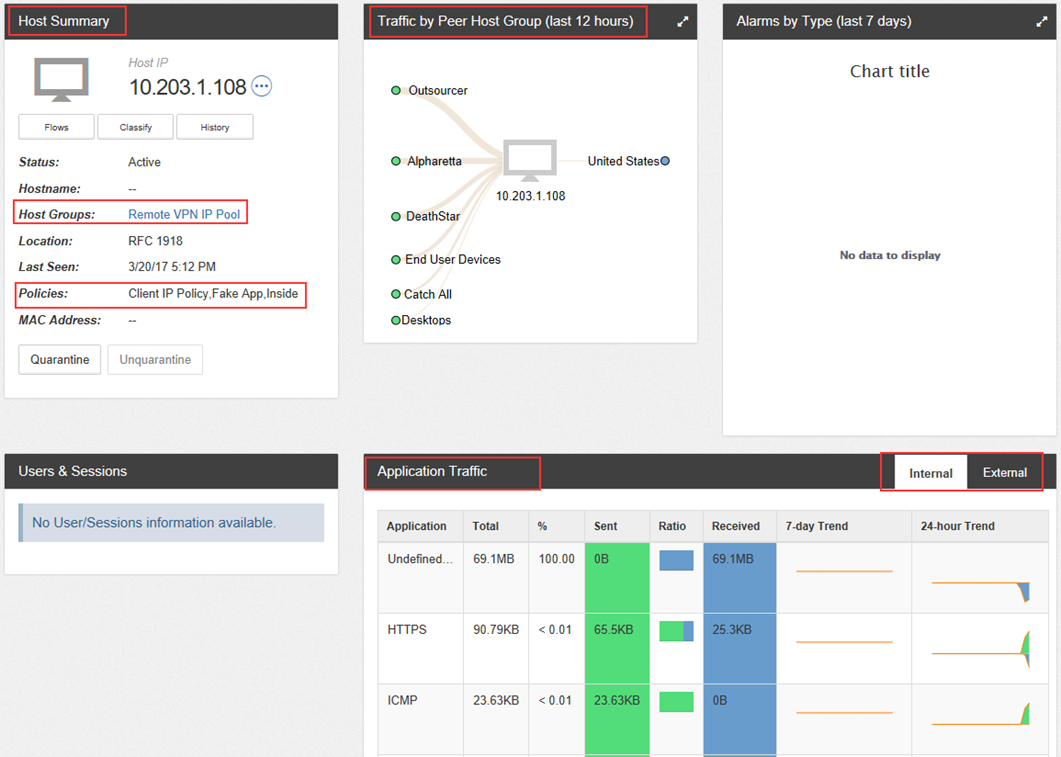
Similarly, we can track all activity with nodes in a group that remote users will interact with.

Please note that in this scenario we did not use the opportunity described yesterday inherent in Ciscco AnyConnect, namely, collecting data about application activity on the host and transferring it to Cisco Stealthwatch Enterprise. In this case, we would have even more information on the activity of the remote nodes.

Having grouped the nodes providing remote access operation, we can apply various policies to them for analysis. For example, quite often, despite preliminary planning, we lack bandwidth due to excessive use of resources, which reduces productivity and may require an increase in resources for remote access. And the reason may be both in the incorrect configuration of the remote access nodes, and in the use of unauthorized software or other abuses on them, including without the knowledge of the owner of the remote computer.
So, how can we use the NTA class solution for analyzing network anomalies for this task. For the host group that interests us, we run the Host Group Application Traffic report.

By default, we see a tab with inbound and outbound traffic for the selected site group. It shows that over the past 4 hours we have outgoing traffic predominantly busy transferring files via P2P.

Further we can receive even more details on outgoing traffic:
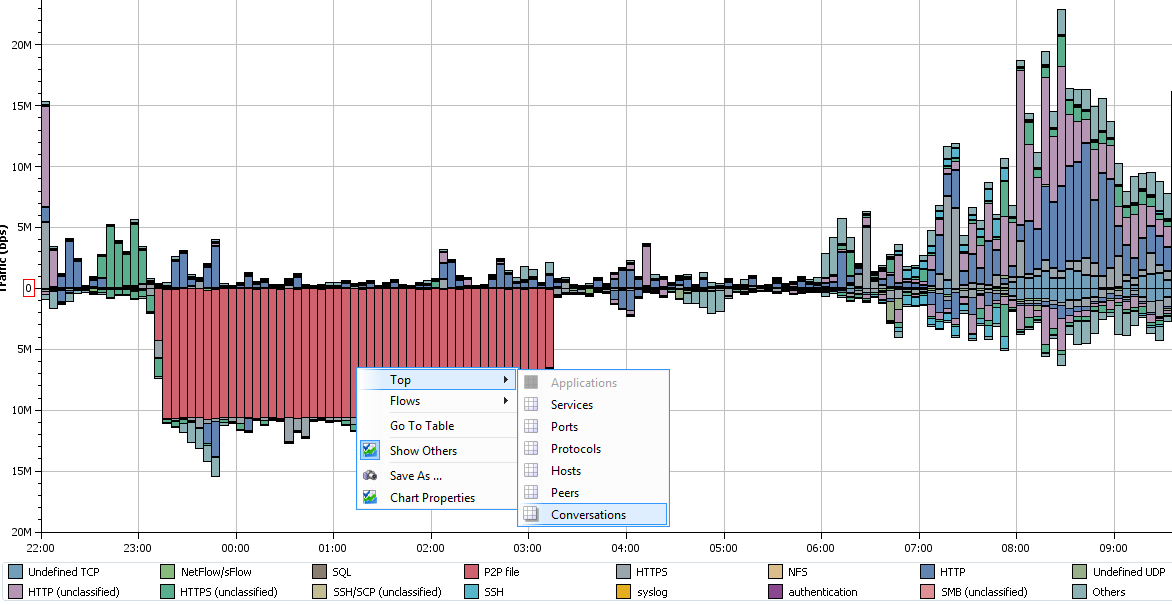
We see interesting statistics as a result – in the first place in terms of the volume of transmitted traffic (17.7 GB) we have an application that transmitted so much data over the 53rd UDP port (this is the DNS protocol).
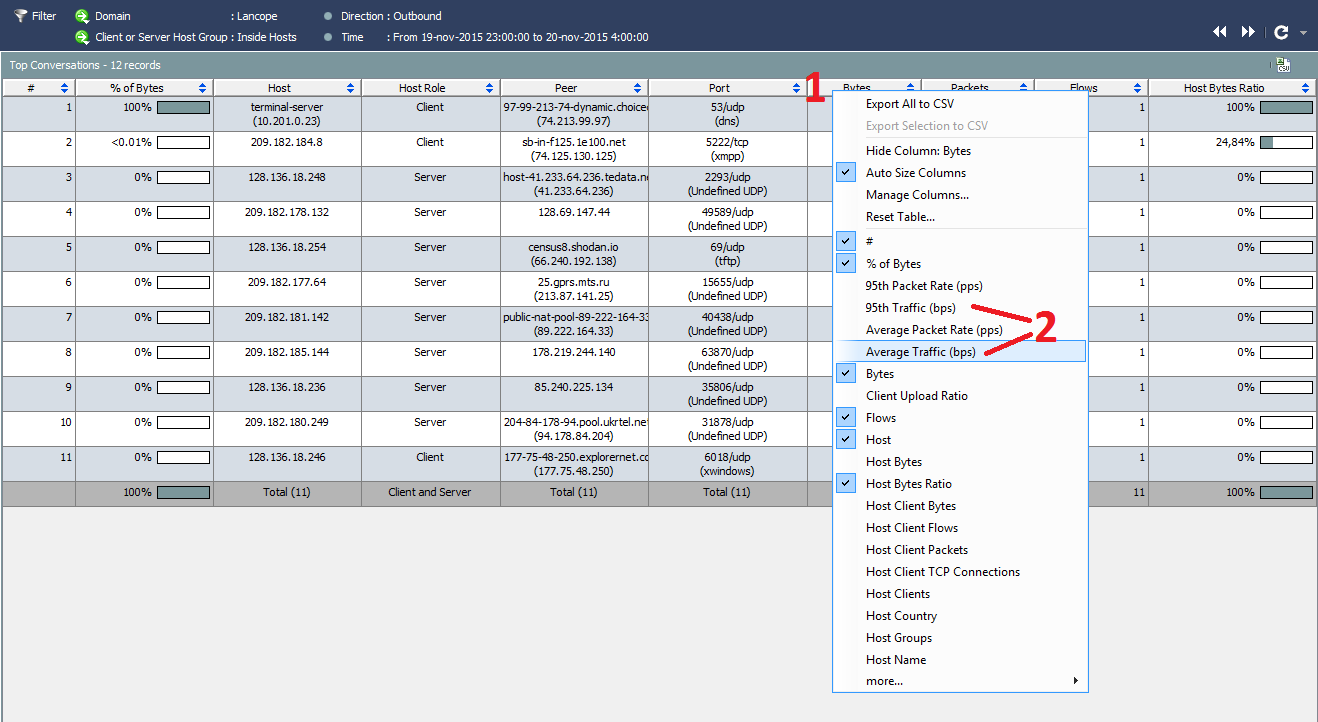
Further, you can conduct a deeper investigation in order to study the nodes with which the node of interest interacted.
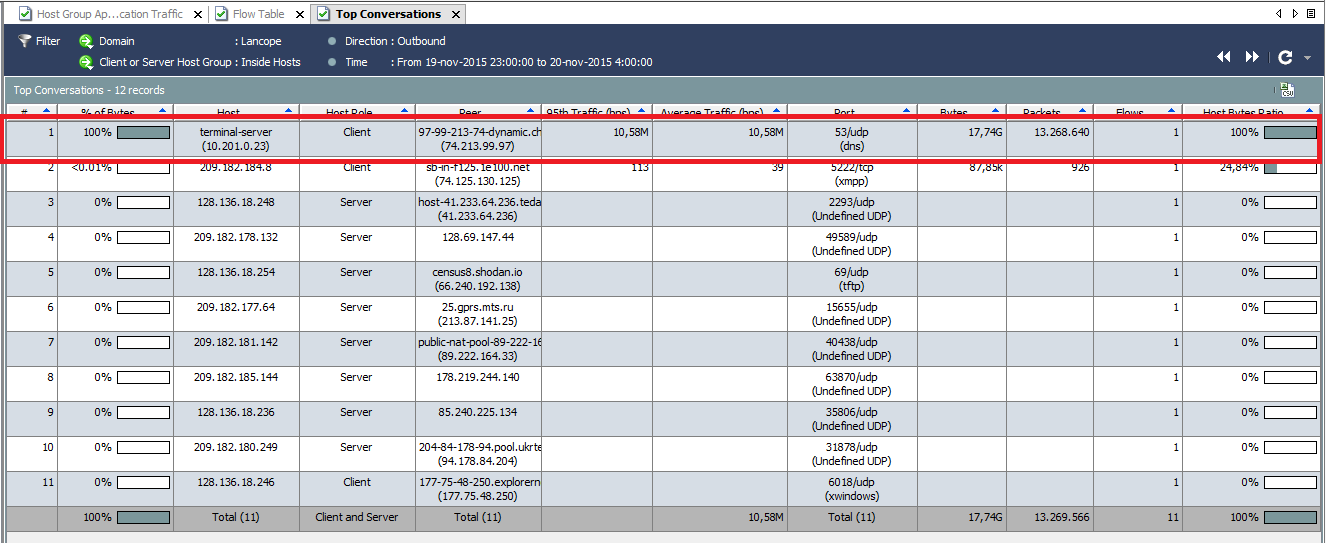
The most interesting thing in this story, of course, is that our peer-to-peer application uses the DNS protocol as a transport for data transfer, which may indicate information leakage or other malicious activity, which is similar to the examples I have already described using NTA- leak control or DNSpionage and Sea Turtle campaign detection solutions.
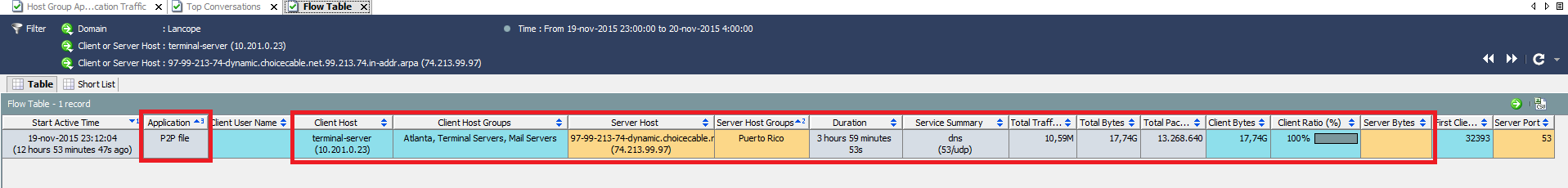
With your Cisco ISE solution in your infrastructure, you can get information not only about the host, but also about the user who violates the security policy requirements. In this case, you can more quickly investigate the incident and respond to it.

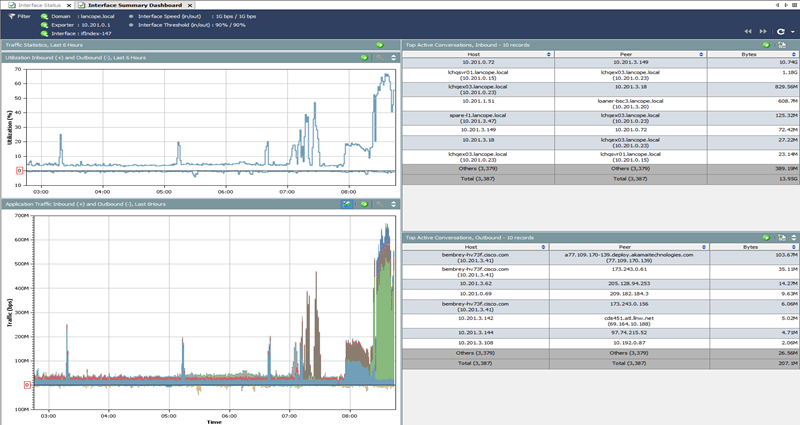
Also, with the help of the NTA-solution, you can fix the excessive use of bandwidth on one or another interface of your network equipment, including those responsible for providing remote access. To do this, just run (and configure the appropriate trigger) report for the interfaces you need:
The Cisco Stealthwatch Enterprise solution, chosen to demonstrate the capabilities of the NTA, allows you to receive recycling on each interface:
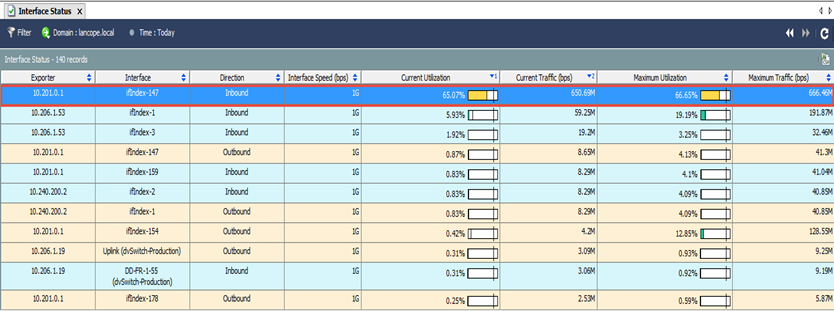
including details on them, including devices and users responsible for using excessive bandwidth:
There seems to be nothing complicated in this scenario and I just wanted to show how easily the solution for analyzing network anomalies can be configured to monitor the remote access segment and identify various anomalies and threats that can come from it. There are two key ideas in this scenario. First, you need to know which nodes you work remotely, and which are located inside your corporate network and what role they play. In general, knowing what your network is and what is the norm in it is the key to success in implementing NTA class solutions, a striking example of which is Cisco Stealthwatch. Secondly, despite the fact that we are talking about monitoring remote access nodes, the traffic from them must somewhere “land” and this “somewhere” is usually located inside the corporate network (case about monitoring remote access in the Desktop-as architecture -a-Service, we will consider DaaS separately), which requires special attention from information security services.
Additional Information:
- Leak Detection Using Network Anomaly Analysis Tools
- DNSpionage Campaign Discovery Using Network Anomaly Analysis Tools
- Malicious code detection using network anomaly analysis tools
- Detecting attacks through browser plug-ins using network anomaly analysis tools
- Cisco Offers Secure Remote Access
- Cisco AnyConnec Secure Remote Access Solution Description
- Flow protocols as a tool for monitoring the security of the internal network
- How does Cisco monitor security on its internal network?