Building a network infrastructure based on Nebula. Part 1 – tasks and solutions

The article will discuss the problems of organizing network infrastructure in the traditional way and methods of solving the same issues using cloud technologies.
For reference. Nebula is a cloud SaaS environment for remote maintenance of network infrastructure. All Nebula enabled devices are managed from the cloud through a secure connection. You can manage a large, distributed network infrastructure from a central location without the effort of building one.
What is the next cloud service for?
The main problem when working with network infrastructure is not network design and equipment procurement, or even rack mounting, but everything else that has to be done with this network in the future.
New network – old worries
When commissioning a new network node, after installation and connection of the equipment, the initial configuration begins. From the point of view of “big bosses” – nothing complicated: “We take the working documentation for the project and start setting up …” This is so great when all network elements are located in one data center. If they are scattered around the branches, the headache with providing remote access begins. Such is the vicious circle: to get remote access over the network, you need to configure the network equipment, and for this you need access over the network …
We have to come up with various schemes to get out of the above impasse. For example, a laptop with Internet access via a USB 4G modem is connected via a patch cord to the configured network. A VPN client comes up on this laptop, and through it the network administrator from headquarters tries to access the branch network. The scheme is not the most transparent – even if you bring a laptop with a pre-configured VPN to a remote site and ask to turn it on, it is far from the fact that everything will work the first time. Especially when it comes to a different region with a different provider.
It turns out that the most reliable way is to keep a good specialist “on the other end of the line” who can customize his part according to the project. If there is no such branch in the staff, there are options: either outsourcing or a business trip.
We also need a monitoring system. It needs to be installed, configured, maintained (at least keep track of disk space, and make regular backups). And who knows nothing about our devices until we tell her. To do this, you need to register settings for all pieces of equipment and regularly monitor the relevance of records.
It’s great when the staff has its own “man-orchestra” who, in addition to the specific knowledge of the network administrator, knows how to work with Zabbix or with another similar system. Otherwise, we take one more person on the staff or we outsource.
Note. The saddest punctures begin with the words: “Why configure this Zabbix (Nagios, OpenView, etc.)? I’ll quickly pick it up and it’s done! “
From implementation to operation
Let’s consider a specific example.
An alarm message was received that the WiFi access point is not responding somewhere.
Where is she?
Of course, a good network administrator has his own personal reference book in which everything is written down. Questions start when this information needs to be shared. For example, you urgently need to send a messenger to sort it out on the spot, and for this you need to give something like: “Access point in the business center on Stroiteley Street, building 1, on the 3rd floor, office 301 next to the entrance door under the ceiling. “
Let’s say we are lucky and the access point is powered via PoE, and the switch allows it to be rebooted remotely. You don’t have to go, but you need remote access to the switch. It remains to configure port forwarding through PAT on the router, deal with VLAN for connecting from outside, and so on. It’s good if everything is set up in advance. The work may not be difficult, but it needs to be done.
So, the power point was rebooted. Did not help?
Let’s say there is something wrong with the hardware. Now we are looking for information about the warranty, the start of operation and other details of interest.
Speaking of WiFi. Using the home version of WPA2-PSK, in which one key for all devices, is not recommended in a corporate environment. Firstly, one key for all is simply unsafe, and secondly, when one employee leaves, then you have to change this shared key and re-configure the settings on all devices for all users. To avoid such troubles, there is WPA2-Enterprise with individual authentication for each user. But this requires a RADIUS server – another infrastructure unit that needs to be monitored, backed up, and so on.
Please note that at every stage, be it implementation or operation, we used support systems. This is a laptop with “third-party” Internet access, and a monitoring system, and a reference base for equipment, and RADIUS as an authentication system. In addition to network devices, you also have to maintain third-party services.
In such cases, you can hear the advice: “Give it to the cloud and not suffer.” For sure there is a cloudy Zabbix, maybe there is a cloudy RADIUS somewhere, and even a cloud database to keep a list of devices. The trouble is that this is not needed separately, but “in one bottle.” And all the same, the questions of organizing access, initial configuration of devices, security and much more arise.
What does it look like when using Nebula?
Of course, initially, the “cloud” knows nothing about our plans or the purchased equipment.
First, an organization profile is created. That is, the entire infrastructure: headquarters and branches is first registered in the cloud. Requisites are specified, accounts for delegation of authority are created.
There are two ways to register the devices you are using in the cloud: the old-fashioned way – simply by entering the serial number when filling out a web form or by scanning the QR code using your mobile phone. All you need for the second method is a smartphone with a camera and Internet access, including through a mobile provider.
Of course, Zyxel Nebula provides the necessary infrastructure for storing information, both accounting and settings.
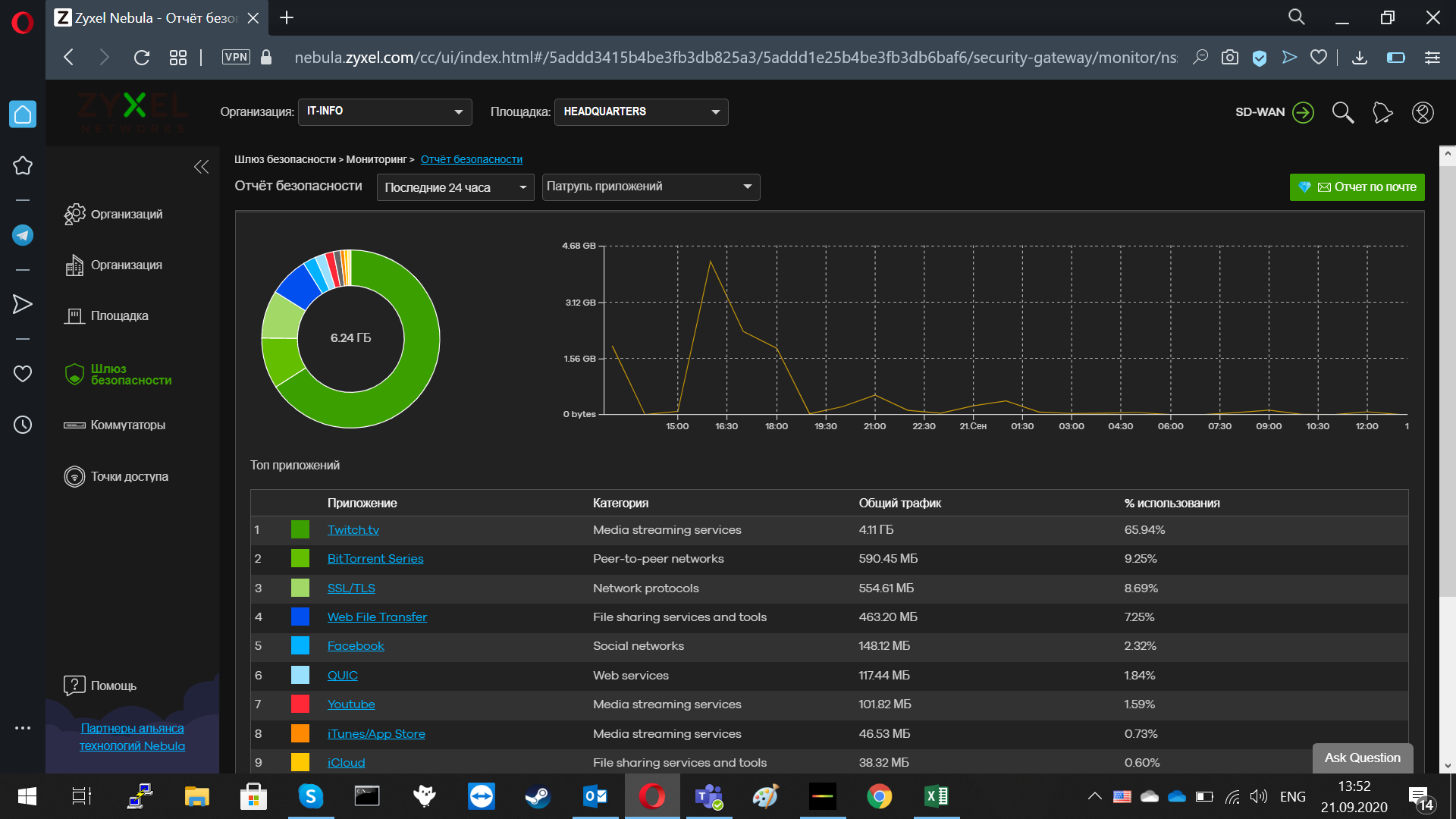
Figure 1. Security report of the Nebula Control Center.
And what about the access settings? By opening ports, forwarding traffic through an incoming gateway, by all that security administrators affectionately call: “pick holes”? Fortunately, you don’t need to do all this. Devices running Nebula establish an outbound connection. And the administrator for configuration is connected not to a separate device, but to the cloud. Nebula mediates between two connections: to the device and to the network administrator’s computer. This means that the stage with a call to the incoming admin can be minimized or skipped altogether. And no additional “holes” in the firewall.
What about the RADUIS server? After all, you need some kind of centralized authentication!
And these functions are also taken over by Nebula. Authentication of accounts for access to equipment goes through a secure database. This greatly simplifies the delegation or revocation of rights to manage the system. You need to transfer the rights – we get a user, assign a role. It is necessary to take away the rights – we perform the opposite actions.
Separately, it should be said about WPA2-Enterprise, which requires a separate authentication service. Zyxel Nebula has its own counterpart, DPPSK, which allows WPA2-PSK to be used with an individual key for each user.
“Inconvenient” questions
Below we will try to give answers to the most tricky questions that are often asked when entering the cloud service.
Is it really safe?
In any delegation of control and management, two factors play an important role in ensuring security: anonymization and encryption.
The use of encryption to protect traffic from prying eyes is more or less familiar to readers.
Anonymization hides information about the owner and source from the cloud provider’s staff. Personal information is removed and records are assigned a “faceless” identifier. Neither the cloud software developer nor the cloud administrator can know the owner of the requests. “Where did this come from? Who might be interested in this? ”- such questions will remain unanswered. Lack of ownership and source data makes insider a waste of time.
If you compare this approach with the traditional practice of outsourcing or hiring an incoming admin, it is obvious that cloud technologies are safer. An incoming IT specialist knows a lot about his organization, and can, willingly or unwillingly, cause significant harm in terms of security. Still need to resolve the issue of dismissal or termination of the contract. Sometimes, in addition to blocking or deleting an account, this entails a global change of passwords for accessing services, as well as an audit of all resources for “forgotten” entry points and possible “bookmarks”.
How much is Nebula more expensive or cheaper than the incoming admin?
Everything is relative. Basic Nebula features are available for free. Actually, what could be even cheaper?
Of course, you cannot completely do without a network administrator or a person replacing him. The question is in the number of people, their specialization and distribution by sites.
As for the paid extended service, then to pose a direct question: is it more expensive or cheaper – this approach will always be imprecise and one-sided. It would be more correct to compare many factors, ranging from money to pay for the work of specific specialists and ending with the costs of ensuring their interaction with a contractor or individual: quality control of performance, drawing up documentation, maintaining a level of security, and so on.
If we talk about whether it is profitable or not profitable to purchase a paid service package (Pro-Pack), then an approximate answer may sound like this: if the organization is small, you can get by with the basic version, if the organization is growing, then it makes sense to think about the Pro-Pack. The difference between the Zyxel Nebula versions can be seen in Table 1.
Table 1. Differences in feature sets between base and Pro-Pack for Nebula.
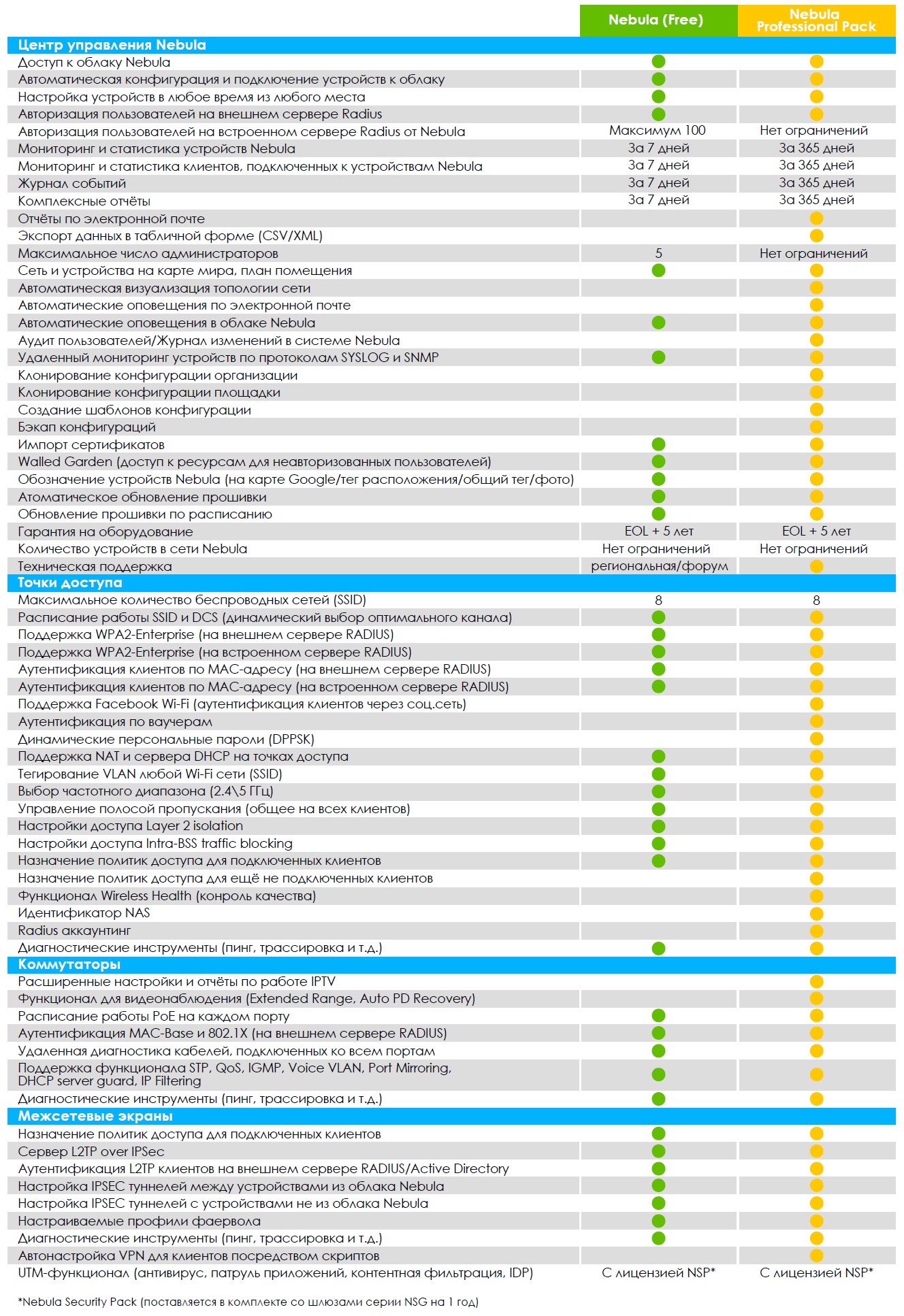
This includes advanced reporting, user auditing, configuration cloning, and much more.
What about traffic protection?
Nebula uses the protocol NETCONF to ensure the safety of working with network equipment.
NETCONF can run on top of several transport protocols:
If you compare NETCONF with other methods, for example, management via SNMP, it should be noted that NETCONF supports outbound TCP connection to overcome the NAT barrier and is considered more reliable.
What’s with hardware support?
Of course, you shouldn’t turn the server room into a zoo with representatives of rare and endangered types of equipment. It is highly desirable that the equipment united by the control technology covers all directions: from the central switch to the access points. Zyxel engineers took care of this possibility. There are many devices running Nebula:
central switches 10G;
access level switches;
PoE switches
access points;
network gateways.
Using a wide range of supported devices, you can build networks for various types of tasks. This is especially true for companies that do not grow up, but in breadth, constantly mastering new sites for doing business.
Continuous development
Network devices with a traditional control method have only one way of improvement – changing the device itself, whether it be new firmware or additional modules. In the case of Zyxel Nebula, there is an additional path for improvement – through improving the cloud infrastructure. For example, after updating the Nebula Control Center (NCC) to version 10.1. (September 21, 2020) new features are available to users, here are some of them:
The owner of the organization can now transfer all ownership rights to another administrator in the same organization;
a new role called Owner’s Representative, which has the same rights as the owner of the organization;
new organization-wide firmware update feature (Pro-Pack feature);
two new options have been added to the topology: device reboot and PoE port power on and off (Pro-Pack function);
support for new models of access points: WAC500, WAC500H, WAC5302D-Sv2 and NWA1123ACv3;
support for voucher authentication with printing QR codes (Pro-Pack function).