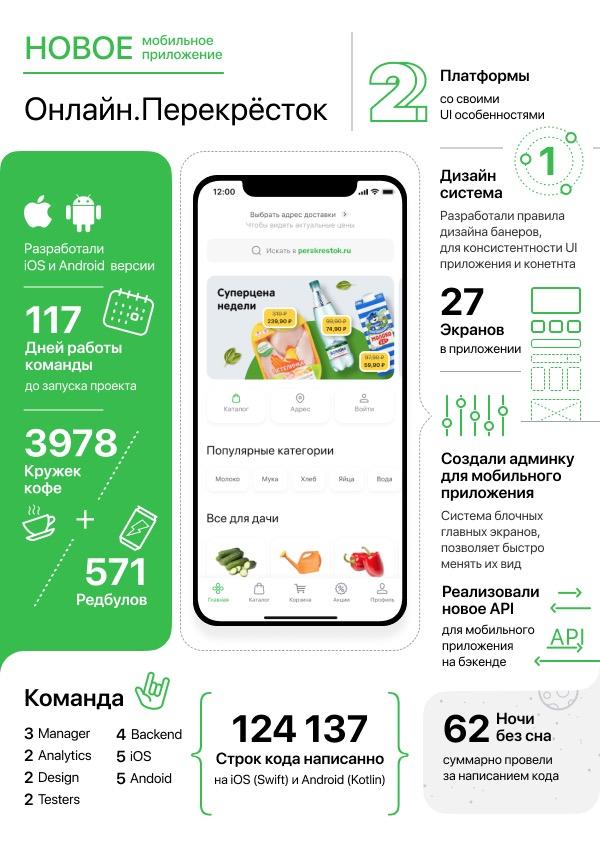
8. Fortinet Getting Started v6.0. Work with users
Greetings! Welcome to the eighth lesson of the course Fortinet getting started. In the sixth and seventh lessons, we got acquainted with the basic security profiles, now we can release users to the Internet, protecting them from viruses, delimiting access to web resources and applications. Now the question is about administering user records. How to provide Internet access only to a specific group of users? How can one group of users be banned from visiting certain websites and another is allowed? How to integrate existing FortiGate firewall user record control solutions? Today we will discuss these issues and try to do everything in practice.
First, let’s look at the authentication methods that FortiGate supports. There are essentially two of them – local and remote. 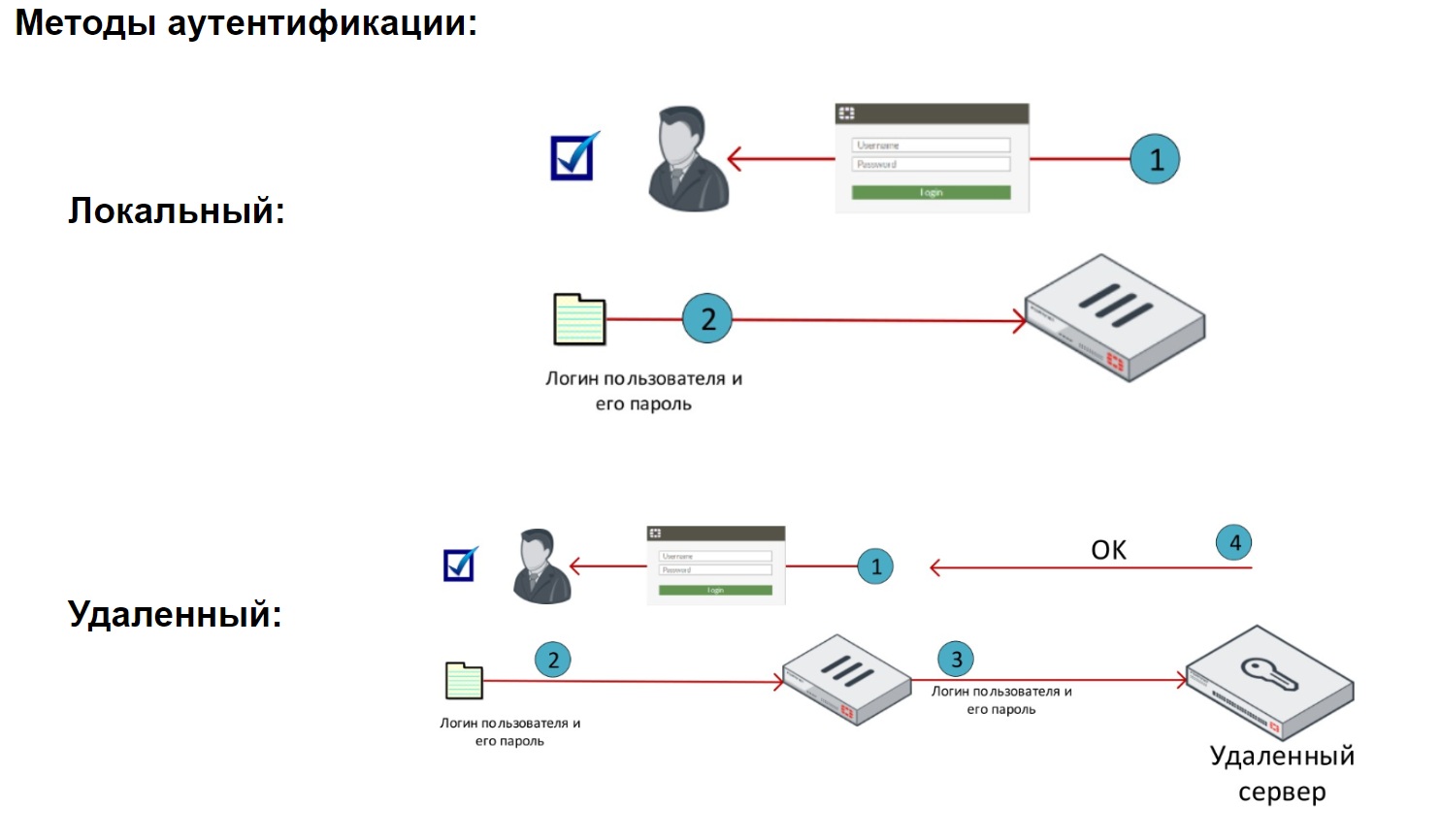
The local method is the simplest authentication method. In this case, user data is stored locally on FortiGate. Local users can be grouped. And based on users or groups to differentiate access to various resources.
When using remote authentication, users authenticate to remote servers. This method is useful when several FortiGate need to authenticate the same users, or when an authentication server is already on the network.
When a remote server authenticates users, FortiGate sends the credentials entered by the user to this server. This server in turn checks whether such credentials are present in its database. If so, the user is successfully authenticated in the system.
It is worth noting that in this case, user credentials are not stored on FortiGate, and the authentication process takes place on a remote server.
It is also worth mentioning the Fortinet Single Sign On mechanism. It allows you to organize transparent authentication of domain users on FortiGate using data from domain controllers. Unfortunately, consideration of this mechanism is beyond the scope of our course.
FortiGate supports many types of authentication servers, such as POP3, RADIUS, LDAP, TACAS +. We will consider working with an LDAP server.
The video discusses the basic theory, as well as working with local users and an LDAP server.
In the next lesson, we will consider working with logs, in particular, we will consider the possibilities of FortiAnalyzer solution. In order not to miss it, stay tuned for updates on the following channels: