3CX security basics. Part 2
Hello!
This is the second article on 3CX security. As promised, in it we will talk about the best practices for securing 3CX. Let’s start without preamble, going through the main sections of the interface that you need to pay attention to.
Enable Global IP Blacklist

3CX Global IP Blacklist – an important security feature that is enabled by default after installing 3CX. It allows you to automatically block IP addresses suspected of various attacks. Systems where this feature is disabled are immediately at risk. If the blacklist does not work, unsuccessful registration attempts from fake SIP user-agents – Polycom VVX, Asterisk, Avaya, etc. will appear in the PBX event log. This indicates a large number of crawler bots trying to break through the PBX with a brute force attack (get SIP registration instead of a legal user). Attacks usually come from behind a VPN, from a compromised server or SIP device. However, they can also come from a completely legal server that is configured incorrectly (in this case, it becomes an open relay of SIP requests – hackers send you REGISTER requests on behalf of foreign servers).
Restrict access to ports
If you keep even some PBX ports open to the whole world, expect trouble. For example, SIP port 5060 (UDP/TCP) should only be open to a few trusted IP addresses. Usually these are the addresses of your remote offices and connected SIP operators. We list typical configuration errors.
Accessing the IP phone interface “from the world”
Sometimes a situation arises when the web interface of the phone or gateway is freely available via the Internet. Often the administrator himself opens HTTP / HTTPS ports on the WAN interface of the router to remotely configure devices. Never do this! Open ports entail a number of serious risks:
Vendor firmware may have vulnerabilities and updates are not made or not made on time
Default vendor password left on hardware
Possible zero-day vulnerability when it is found on a popular device and immediately exploited by hackers
The search for vulnerable devices is done using specialized systems such as Shodan.
All your VoIP equipment must be located behind NAT and not be accessible from the outside world. If you need remote access, install the remote administration software on one of the internal computers and connect to devices through it.
SSH port access
When you open the standard SSH port (TCP 22) to control Linux, it will be the target of constant brute force attacks. You will see the auth.log Syslog file (records of login attempts from various IP addresses) growing.
Combination of different services
If there are other applications running on your 3CX server, this increases the vulnerability of the system as a whole. For example, additional web services are a potential target for attacks. The general rule is to close all the ports that are possible, leaving only critical ones for 3CX to work. This is done by properly configuring your firewall.
Protect your backups with a password
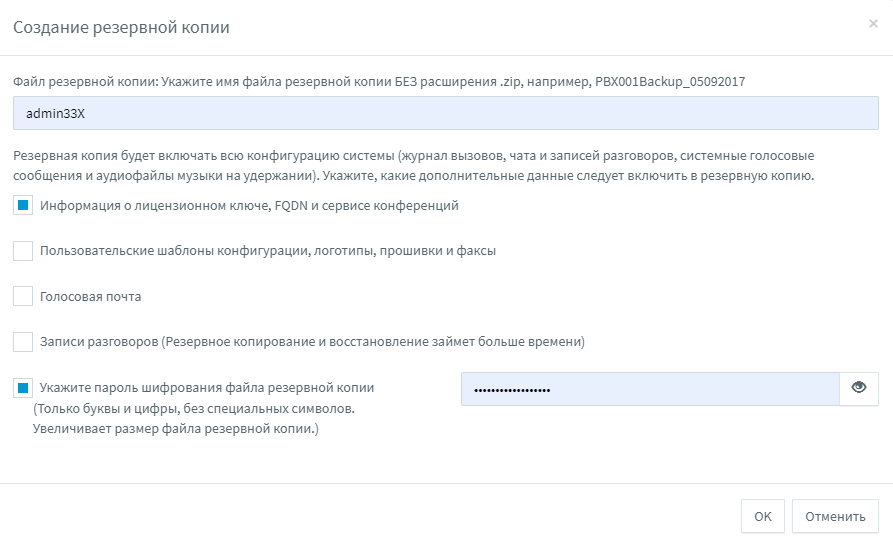
We have seen cases of systems being hacked through a stolen backup file. Therefore, we recommend using backup encryption on all your systems, and with different passwords. Also, do not use a single storage for all backups – if it is compromised, attackers will gain access to all your systems at once. Also, the storage can fail – and this will be a single point of failure.
Restrict access to the management interface

Set from which addresses the administrator can generally manage 3CX. Connection from another IP, even with correct credentials, will be rejected.
Turn on email notifications
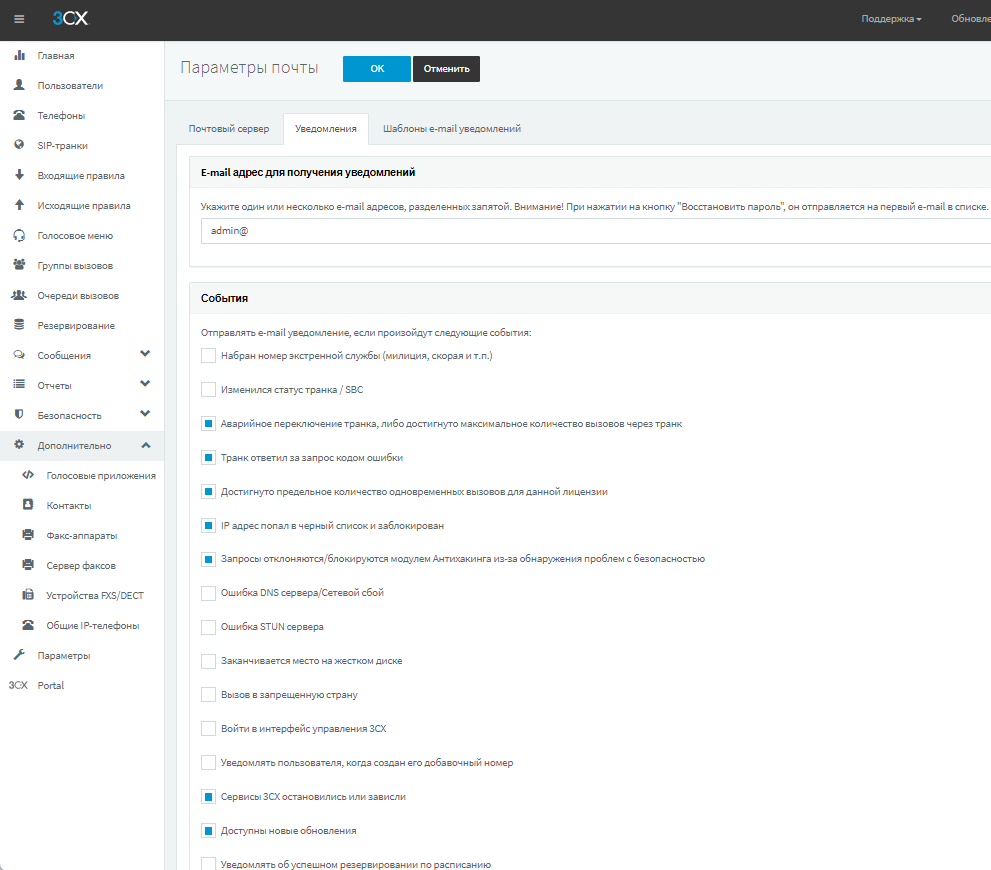
3CX provides various e-mail notifications for real-time PBX monitoring. They allow you to quickly receive information about suspicious events related to calls and security. We recommend that you enable these notifications and specify several e-mail addresses of administrators separated by commas. Notification settings are located in Options > Mail. The table below describes the events that trigger the system to send notifications.
EVENT NAME IN E-MAIL | EVENT DESCRIPTION |
Trunk failover or maximum number of calls through trunk reached | The actual number of calls exceeded the parameter specified in the trunk field “Number of simultaneous calls” |
The trunk / provider responded to the request with an error code | The call was rejected, for example, by the telecom operator |
The limit for the number of simultaneous calls for this license has been reached | Users making too many simultaneous calls |
IP address is blacklisted and blocked | IP address blocked by PBX server due to repeated registration attempts with incorrect credentials |
Requests are rejected/blocked by the Anti-Hacking module due to the detection of security issues | The IP address was blocked after sending too many requests (flood/DoS) |
Call to a banned country | The user tried to dial an international number with an illegal country prefix |
View the audit log

3CX v18 introduced the audit log. If enabled, the administrator will be able to track any changes made in the PBX management interface (by another administrator or a user with the appropriate rights). Each event in the log contains a timestamp, username, user IP address, and a log of the change made (before and after parameters). The audit trail is enabled on the Home page. Review it periodically for any unusual changes. Content can also be exported to CSV format.
Protection on the side of your operator
In addition to the settings on the 3CX side, VoIP operators also provide customers with additional security tools. Log in to your account with the operator and look for the following parameters:
Call restrictions by country – set similar to 3CX settings
Maximum number of simultaneous calls through an operator
Limit of funds and prohibition of automatic replenishment of the balance
Email notification and automatic account blocking when suspicious calls appear
Summary
Our advice may seem trite. Strictly speaking, they are worth nothing if you simply read them. But if you spend half an hour of your time and go through the settings that we talked about, you will potentially avoid a huge hassle and confirm your reputation as a professional!





